
The Factory Reset Myth: Why Your Wiped Device Still Holds Secrets
Think your device is fresh after a factory reset? Hidden fragments of your life may still be buried inside from personal chats to financial details. Discover the dirty truth about resets and how to protect your data before selling or recycling.

The Document Attachment Scam: Beware of Curiosity Traps
Beware the rising document attachment scam. Empty emails with fake files trick victims into opening malware. Learn how to spot and avoid it.

Why Your Scam-Detection Tactics Are Failing in 2025 (and What to Do Instead)
Think you can spot a scam because you hear their voice, see them on video, or call back a “real” number? In 2025, AI scams, deepfakes, and spoofed calls make those checks obsolete. Learn the new tactics scammers use and how to truly protect yourself.

Say Yes Phone Scam: How Scammers Use Your Voice to Hack You in 2025
You think a phone call is harmless, but AI scams have changed the rules. Learn how one word can let criminals clone your voice and bypass security.

Don’t Fall for This Common Trap; How to Spot Fake Online Courses Before It’s Too Late
Learn how to spot fake online courses before paying. Protect your time, money, and data with these proven tips to avoid education scams.

What Nobody Tells You About Smart Doorbells and How They Might Be Spying on You
Imagine purchasing a smart doorbell to enhance your home’s security, only to discover it might be compromising your privacy. This scenario is increasingly becoming a reality. Smart doorbells, designed to monitor your front door, can collect sensitive data, transmit it to third parties, and potentially be exploited by hackers. As homes become more connected, devices…

Before You Download That Job PDF, Read This First
Discover how hackers hijack job forms with malicious PDFs and what you can do to stop them. Learn about the techniques, detection methods, and prevention strategies.

The Real Reason That “Call from Mom” Might Not Be Real
Learn how to spot and stop AI voice cloning scams. Discover how these scams work, real-life examples, how to detect fake voices, and steps to protect your identity and finances.

What Nobody Tells You About How Your Smart TV Might Be Spying on You
Smart TVs are now a central part of home entertainment. They offer on-demand content, voice assistants, app stores, and even video calling. But as the “smart” part of these TVs gets more advanced, so do the privacy concerns. Today, many people are asking: Can my smart TV spy on me? The short answer is yes.…

You Might Be Hacked If Your Phone Is Doing These 6 Things on Its Own
In today’s interconnected world, our smartphones are extensions of ourselves holding personal photos, sensitive messages, financial information, and more. But what if someone else had access to all of that without your knowledge? The unsettling reality is that remote access to smartphones is not just a plot in spy movies; it’s a genuine threat that…
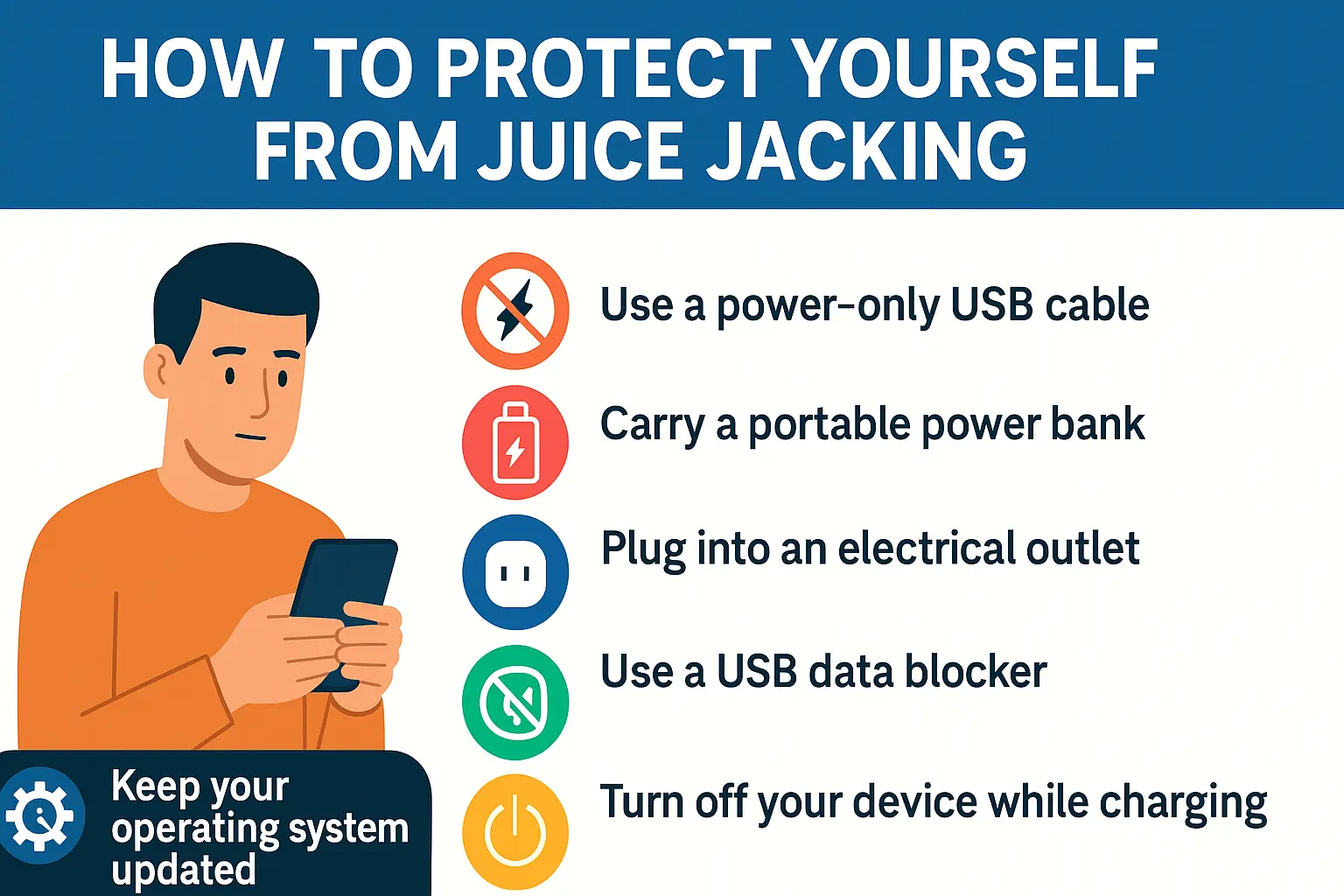
Don’t Make This Charging Mistake; It’s How Hackers Infect Your Phone
Public charging stations may seem like a modern convenience, especially when your phone battery is low and you are far from home. Found in airports, cafes, shopping malls, and hotels, these charging ports offer quick relief. But beneath the surface lies a growing cyber threat that most users do not expect. Cybercriminals have figured out…

The One URL Trick That Changes How You Spot Scams Forever
Cybercriminals are getting more clever at hiding in plain sight. Today, one of the most common ways people fall victim to scams is by clicking on fake websites that look real. These websites are often just one character away from a trusted brand, and unless you know how to read URLs like a hacker, you…

Is Your Phone Camera Watching You Without Permission? What You Need to Know
In a world where smartphones are used for almost everything, one unsettling question continues to surface: can my phone camera be hacked without me knowing? The short answer is yes. Hackers can gain access to your phone’s camera remotely, often without any visible signs. While this might sound like something out of a spy movie,…
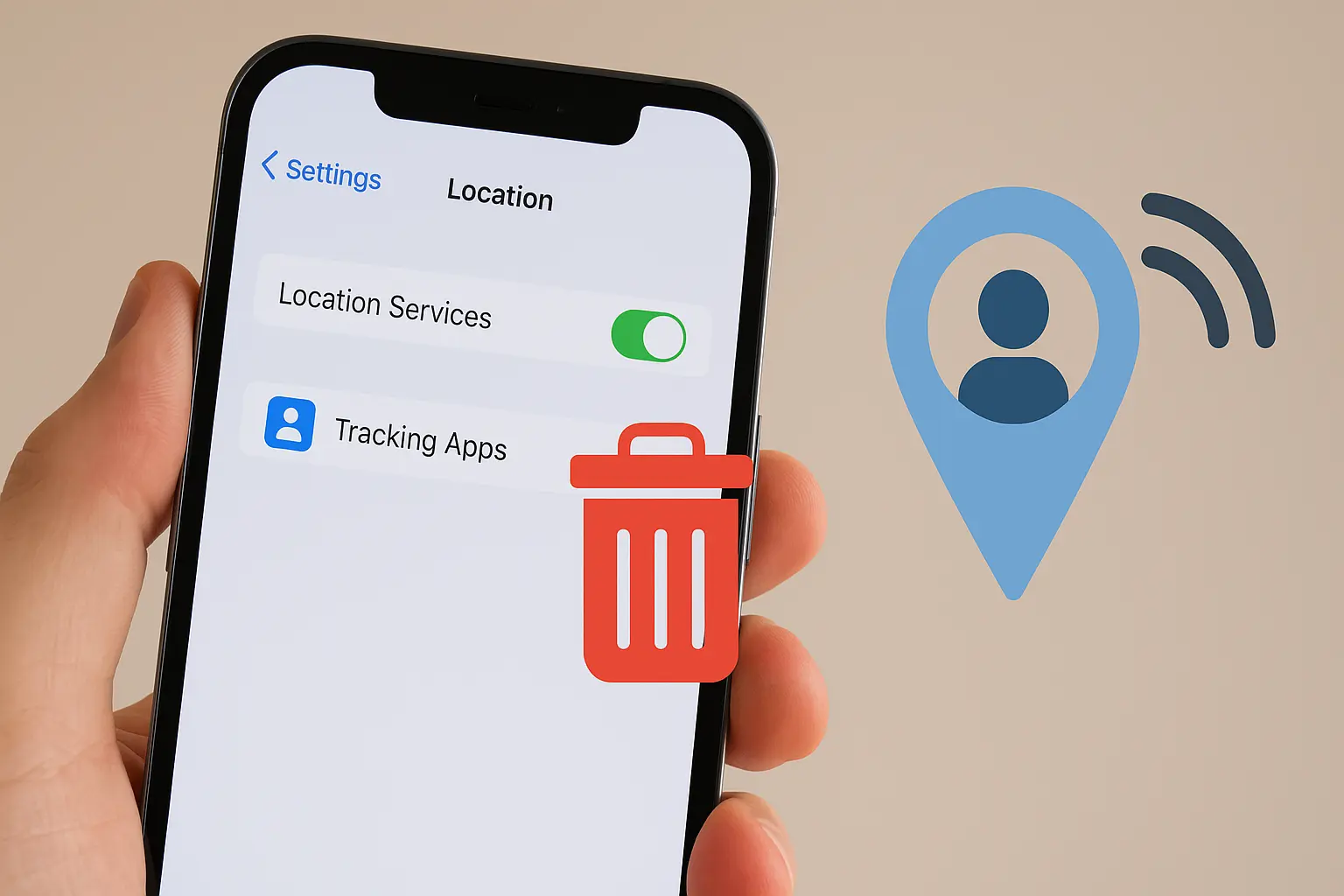
You’re Not Crazy; Your Phone Might Actually Be Tracking You
Today, privacy has become more than a luxury. It is a necessity. Tracking apps have quietly infiltrated smartphones, monitoring activities, gathering sensitive information, and compromising security. If you are searching for how to clear your phone of tracking apps, you are in the right place. This guide will show you how to detect, remove, and…

Before You Click “Close”, Read This About Pop-Up Scams
Think closing a pop-up scam window keeps you safe? You might be overlooking a critical mistake that leaves your data vulnerable. Don’t wait until it’s too late to protect yourself. We have all been there—annoying pop-ups interrupting our browsing. But what if I told you that harmlessly clicking the ‘close’ button could expose your personal…

Don’t Make This Mistake Linking Instagram to Facebook: It Could Get You Banned
The question might be, is Meta disabling people’s accounts because they are linked to Instagram or Facebook? The answer is no. You can have your Facebook and Instagram accounts linked together and still not get your accounts disabled.

The Real Reason Phishing Attacks Still Work in 2025
Phishing is a form of social engineering and a scam where attackers deceive people into revealing sensitive information or installing malware such as viruses, worms, adware, or ransomware.

10 Cybersecurity Habits Every Employee Should Be Following Now
In the current digital environment, businesses of all sizes are increasingly vulnerable to various cyber threats. While companies invest in security tools and technologies, employees are essential in upholding cybersecurity. In fact, employees often act as the first line of defense in safeguarding a company’s sensitive data and systems.

The Real Reason Ransomware Keeps Spreading and How to Protect Yourself
Ransomware has emerged as one of the most pervasive and damaging cyber threats in recent years. Its consequences can be devastating, affecting individuals, businesses, and even critical infrastructure.

You Don’t Need to Be a Cybersecurity Expert to Protect Your Small Business
This article will look at ways to maintain a strong cybersecurity posture for businesses without the infrastructure, resources, or requirement to justify using the current, sometimes costly corporate cyber model.

How to Spot ATM Skimmers Before They Steal Your Card Info
We’ve all been in that situation where we are trying to withdraw some cash, possibly in a hurry, and not thinking much beyond punching in our PIN and grabbing our money. But what if, in those few moments, someone managed to steal your card information without you even realizing it?

How to Keep Hackers Out of Your Wi-Fi; No Tech Skills Required
Who helped you set up your home or small business internet router? It doesn’t matter if it was done by your internet service provider, another technician, or you.

Before You Give Up; Here’s How to Break Into Cybersecurity Without a Tech Background
Are you struggling to break into a career in cyber security with no experience? Are you struggling to get a job after your cyber security degree?

2 Hard Truths About IT Skills That Won’t Make You Money Fast
Learning the wrong IT skills is more like going back to school. You will have the skills but will not know where to use them.

This Might Be Why Money Disappears from Your Bank Account Without a Trace
Is it possible for you to wake up one day and realize that the money in your bank account is gone? The answer is yes, money can disappear from your bank account without your authorization.

What Nobody Tells You About Sextortion Until You’re Targeted
Is someone threatening to share your nude picture online? Have you sent your nude to someone on social media before? Or do you engage in sexting or watch porn online?
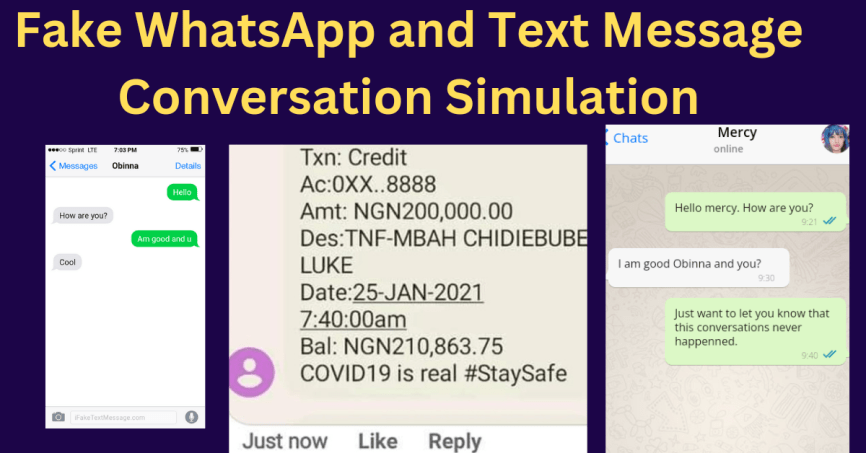
This Might Be Why You Believed That Fake WhatsApp Chat Was Real
Every internet user should be conscious of fake WhatsApp or text message conversations.

The Real Reason People Still Get Hacked Through Phone Calls
It is not news of people complaining about being hacked through phone calls.
Have you heard of people claiming they lost money in their bank account after answering a phone call?

Don’t Make This Mistake When Applying for Jobs, It Could Be a Scam
The rate of online job scams is growing and the tactics used are also advancing. Gone are the days when online scammer’s tricks look so shabby and unprofessional.

Alarming New Internet Fraud Tactics: How to Avoid Becoming a Victim
The internet fraud landscape is really changing. Getting hacked or scammed is becoming much easier as the days go by and technology advances.

The Real Reason Watching Porn Can Get You Hacked; And How to Stay Safe
Some people are carrying key loggers on their mobile phones or computer today because they visited a porn website.
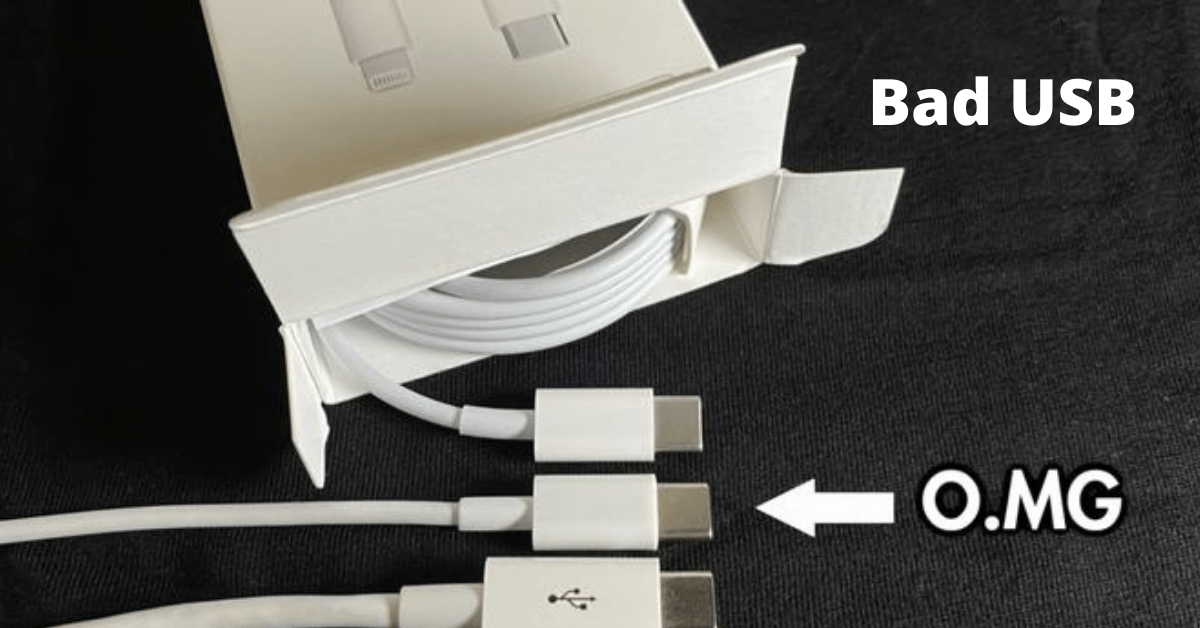
Don’t Make This USB Charging Mistake; Hackers Use It to Hijack Your Phone
Have you heard about OMG cable before? When last did you borrow a USB charger from people to charge your phone?

It’s Not Too Late to Take Your Privacy Seriously: Why Tails OS Might Be What You Need
The Tails operating system (OS) is a free portable operating system that helps its users avoid surveillance, censorship, advertising, and viruses. Tails is designed for privacy protection. The surveillance, censorship, virus, and privacy protection features of Tails are very important, but one thing that makes Tails interesting is its portability. This means that you can…

You’ve Tried Everything to Avoid Online Scams; Except These Two Simple Tips
Online scammers are improving their tactics daily. The tendency for one to fall victim to them is increasing daily.

16 Cybersecurity Secrets Most Internet Users Never Learn (But Should)
Using the internet without having these cybersecurity secrets at your fingertips makes you more vulnerable to cyberattacks. The internet is now becoming very inevitable for all. If you are not using it to communicate, you may be using it for banking or business transactions. It is also important to note that online activities or transactions…

Before You Click That Link, Read This Guide to Fake Sites
Creating fake websites is easier today than it was before. Even though fake websites are very easy to create these days, it is also very difficult to detect once created.

How to Verify Google AdSense Billing Address Without PIN
Monetizing your blog, personal website, or YouTube using Google AdSense is a cool thing to do. Most times the challenge is always in verifying your AdSense account.

VPN, Proxy, and Onion Services: All You Need to Know
Reasons why many use VPN, Proxy, and Onion services vary, but I believe the common reason is for privacy and anonymity.

Wi-Fi Security Tips You Should Know: Protect Your Network
Wi-Fi is a technology many use for their everyday activities. Like every other technology; it is not immune to security vulnerabilities by default.

They Never Taught You How the Dark Web Works; Here’s What You Should Know Before Using It
What did you hear about the Dark Web? Did you hear it is a place for only bad things? Possibly a place designed for only hackers and criminals, or a dangerous place to visit by ordinary people? If those are what you heard, please read on, as there is more to it.

How You Get Hacked by Clicking Malicious Links: Prevention Tips
With the advent of malicious and phishing links, it is now common cybersecurity advice to tell people to avoid clicking on links.

Detect and Prevent Social Media Scams: A Practical Guide
A greater number of relationships are going to start on social media in the near future.
Turn Your TV into a Personal Computer for Kids with Raspberry Pi
If you consider the amount of time children spend in front of the television watching cartoons or movies, then it will be of great benefit if you convert the television into a personal computer for them.

This Might Be Why Your Calls Aren’t As Private As You Think
A greater percentage of call tapping is activated on our phones by those we are in a relationship with, not always by hackers.

Cryptocurrency Cybersecurity Tips for Beginners: 2024 Guide
With the surge in the price of Bitcoin, the desire to invest in cryptocurrency has increased for many.

Detect and Remove Spyware from Your Phone: A Working Guide
There is a possibility that someone somewhere is monitoring you on your phone using spyware.
Enable Secure DNS or DoH on Your Browser: A Security Guide
DNS Over HTTPS (DoH) is a protocol designed to give internet users great power over their browsing experience.

How to Know if Social Media Profile Pictures and Fake Images Are Fake
Detecting fake images by mere looking at them is tending towards impossibility in this age and time.

Protect Your Online Accounts from Hackers: Essential Tips
Having online accounts has become a necessity in the world we are living in today. Whether it is a social media account, an internet banking account, or whatever accounts, the need to protect it from unauthorized users can not be overemphasized.

Recognize Phishing Emails: A Working Guide for 2024
Phishing email is one common way bad actors deliver their hacking tricks and weapons to capture their victims.

Read This Before Your Next Photo: Understanding EXIF Data
If you are someone who loves taking pictures with your phone camera, then you need to know what EXIF data is all about.

Spot Fake Credit/Debit Bank Alerts: Easy Steps for 2024
It has become known over time that one skill internet scammers lack is attention to detail.

Lock Your SIM Card Now: Essential Security Steps
Misplacing or losing our mobile device to theft is a very common situation to experience.

Recover Hacked Facebook Account: A Working Guide for 2024
Recovering a hacked Facebook account after the hacker has changed your email and phone number is difficult but very possible.

Detect Scam and Malicious URLs: Essential Tips for 2024
URLs (Uniform Resource Locator), also known as Web addresses, are the most common tool used by hackers and internet scammers to deliver weapons to their target victims.

How Your WhatsApp Account Gets Hacked & How to Prevent It
Many complain today of their WhatsApp account being hacked, but the question is: was your WhatsApp account really hacked?
What Can a Hacker Do with Your IP Address? Find Out Now
IP stands for Internet Protocol address . It is a number used to identify a device on a network, thereby making communication with the device possible.

Benefits of Multiple User Accounts for Computer Security
Multiple-user support is no longer a feature for computers only; Android phones now come with multiple-user capabilities.

Top Internet Privacy and Anonymity Tools for 2024
One fact about privacy and anonymity tools is that using them on platforms where your identity has been registered makes them useless.

How to Check if You Are Monitored on Social Media: Key Tips
The social media platform is one tool we use that can be used to spy on us by our friends or foes.
Social media applications like Facebook Messenger, Telegram, Instagram, Twitter, etc. can be used concurrently on two phones without one noticing.

6 Social Engineering Countermeasures You Should Know
One of the most common means through which people get hacked these days is through social engineering.

Is This Normal? 7 Signs You Might Already Be Hacked
5 Two-Factor Authentication Mistakes You Might Be Making (And How to Fix Them)
Enabling two-factor authentication for your account is not enough; you also need to avoid these five mistakes.

Website Security Scan-How to Check if a Website is Safe
A website security scan is something you should do whenever you have doubts about the security of a website you intend to visit.

How You Get Hacked: Cybersecurity 101

How You Get Hacked Even With Your Strong Password-Security Vulnerability
One way hackers can get at you is through a security vulnerability in the operating system or applications you use.

Online Security-Five Common Internet Mistakes You Should Avoid

What Nobody Tells You About Posting Online, Until You Get Hacked

How to Check If Your Data Was Exposed in an Online Breach-Data Security

This Might Be Why You Still Fall for Online Scams, Even If You’re Smart
The majority of Internet scammers today see their victims as dumb and greedy people. But the question is; are people really falling victim to internet scams only because they are dumb and greedy?

How to Block Apps From Stealing Your Personal Data From Your Android Phone.
Looking beyond the external security of your Android phone is one shift we all should make for our online security.

How to Use Google Chrome Browser Safety Check
Your browser is another avenue through which bad actors can get at you if it is not secure. Here is good news for Chrome browser lovers.
The Real Reason Your Text Messages Aren’t Safe on Android
Leaving your android phone for 5 minutes in the hands of someone you don’t trust is enough for the person to take over most of your online accounts.

How to Turn on Disk Encryption in Windows 10 Home Edition
Being able to enable Disk encryption is a plus for Windows 10 Home Edition users in terms of physical security.

This Might Be Why Incognito Mode Isn’t Protecting You Like You Think
Incognito mode is a browsing mode that helps you to keep your Internet searches private on a device.

How to Secure Your Google Account: Essential Tips for Better Protection
When you use any of the Google backup tools, securing your Google account should be your major concern.
Because, most of your data will be exposed the moment your account is compromised.
How Hackers Steal Your Passwords, Contacts, and Photos from Google Backup
As our activities online increase, our ability to keep track of our passwords and other details become very difficult. Google backup is one tool we use in making this task easy for us.

How to Recover Phone Contacts Using Telegram: A Simple Guide
Another app that syncs all your contacts to their database is Telegram. This is why you can use it for your contact recovery when needed.
How to Safely Install Apps from Google Play Store: Essential Permission Checks
Clicking install or update all on the Play store is equivalent to granting an app all its app permission on your phone at a go.
Though some Apps might prompt you on first launch to change some App permission settings, but that is not always the case.

How to Check if Your Facebook Account is Secure
Is your Facebook account secure?
Will you like to know if your account is secure or not by just a click of button?
Weak security setup is among the reason why many are losing their Facebook accounts to hackers on a daily basis.

The Real Psychology Behind Online Scams and How to Outsmart Them
Time has passed when falling prey to internet scammers is through a text message that you have won a lottery or a price you never applied for. Or that email from a girl whose father died and want to relocate to your country for you both to get married and claim the father’s wealth.

Before You Lose Access to Facebook; Do These 5 Security Fixes Now

How to Know If Your Windows Computer Is Hacked Already-Working Guide
It is true that when our Facebook or WhatsApp account is hacked, we get kicked out of our personal account, but is the scenario the same when our personal or office computer is hacked? Will we get kicked out of our computer too?
The answer is Yes and No.

Can You Really Read Someone’s WhatsApp Messages? Here’s What You Should Know
Spying on our friends or partners is something some people enjoy doing, but this post is to show you the possibility of people genuinely spying on your WhatsApp messages.

How to Use Google Search Engine for Hacking: A Complete Guide to Google Dorking
Searching for information on Google should not be a struggle at all if you have any of these tips at your disposal.

Passwords You Should Never Use and How to Create a Secure One
Recovering a hacked account is equivalent to hacking the account if the platform you are using does not provide a working account recovery method.

What to Do First When You Lose Your ATM Card in Nigeria: Quick Guide for Immediate Action
Ways to Deactivate Your Lost ATM Card For Different Banks In Nigeria

How to Recover Your Lost Facebook Account: Step-by-Step Instructions
It is funny to know that many are still using their Facebook account today, not because they know their password, but because their device has saved their password and it is now in auto-login.