DNS over HTTPS (DoH) is a protocol designed to give internet users great power over their browsing experience.
It was previously advertised to help protect internet users from being tracked by their ISPs (Internet Service Providers). In other words, it was designed to give internet privacy management to users. But the question remains: did it achieve that?
Or is it one of those hoax privacy and security promises made by tech vendors just to sell their products?
I have always believed that Internet privacy is simply a shift of trust. It is not something you can protect without handing it over to another person. But can DoH prove it wrong?
Before we answer the question of whether DoH is a total hoax or a development to embrace, let us try and understand what DoH is all about.
How Does DNS Over HTTPS (DoH) Work?
Before DoH and even up until now, DNS queries were made in plain text by default. This implies that whoever was able to listen on your network can know the websites you are visiting.
So, before you visit a website like www.confamtips.com, your client browser will at first send a DNS query to the DNS server elsewhere to help resolve the web address you typed to an IP address like 12.32.12.32. It is this IPv4 address that your browser will use as the destination address to request the website resources.
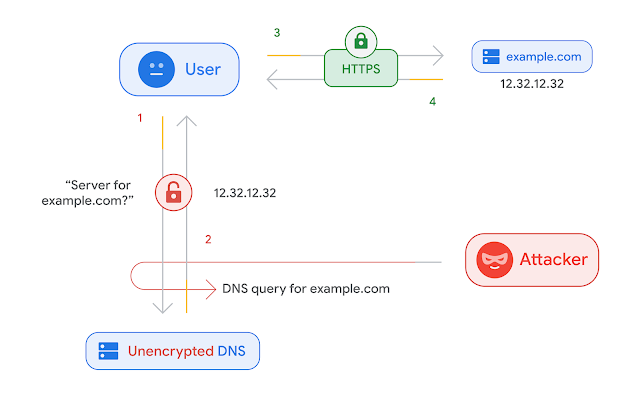
So this request to the DNS server to get the website address resolved to an IP address is called a DNS query. If this query is made unencrypted (that is, without HTTPS), anyone between you and the server you are making the request to can know the websites you are visiting.
Once DNS Over HTTPS is enabled in your browser, the DNS queries will now be encrypted with HTTPS, and anyone listening on your network will not be able to see your queries in cleartext. That means the query will be encrypted.
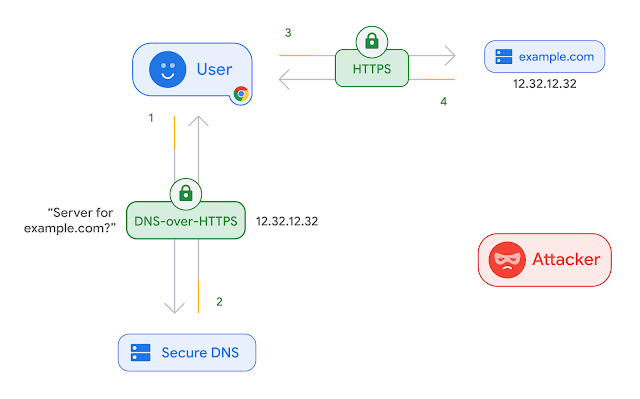
So, using DoH will help to protect you from a man in middle attacks or prying eyes. It also makes it difficult for an attacker to trick you into visiting a fake website through DNS manipulation.
Suggested Post: How to Install Free VPN on Your Android Phone
How to Test If Your Browser is Already Using DNS-over-HTTPS
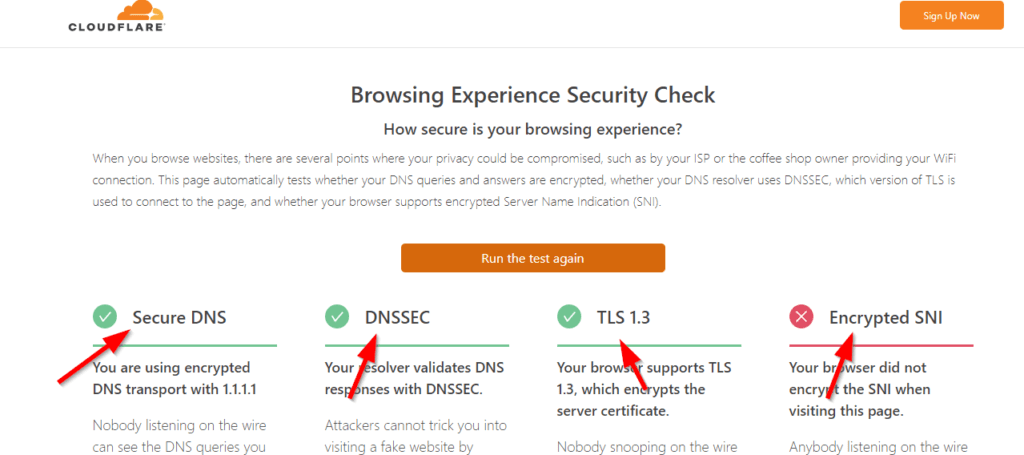
It is easy to test if your browser is already working with a secure DNS. One easy way to run a secure DNS test on your browser is by visiting cloudflare.com/en-gb/ssl/encrypted-sni on the browser you want to test.
Then a web page like the one below will load. Click on the Check My Browser button to run the check. Run the test again, like three times, to be sure the network is working fine before you conclude on the result displayed.
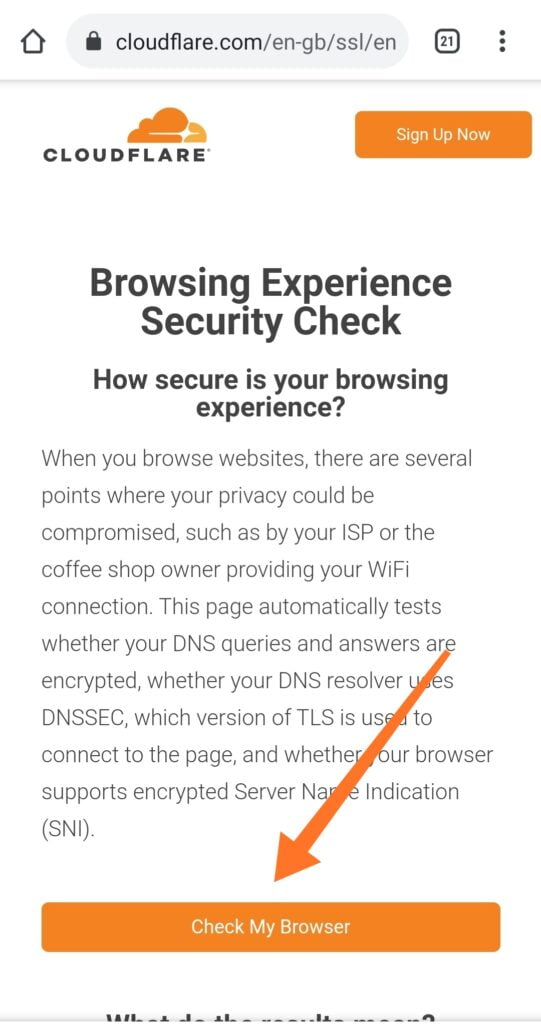
If Secure DNS is enabled, it will be marked as good. The same tick will be given to DNSSEC and TLS. It will also test if your browser supports encrypted Server Name Indication (SNI), which is not supported by many browsers as of the time of this post. So you might get worse at that.
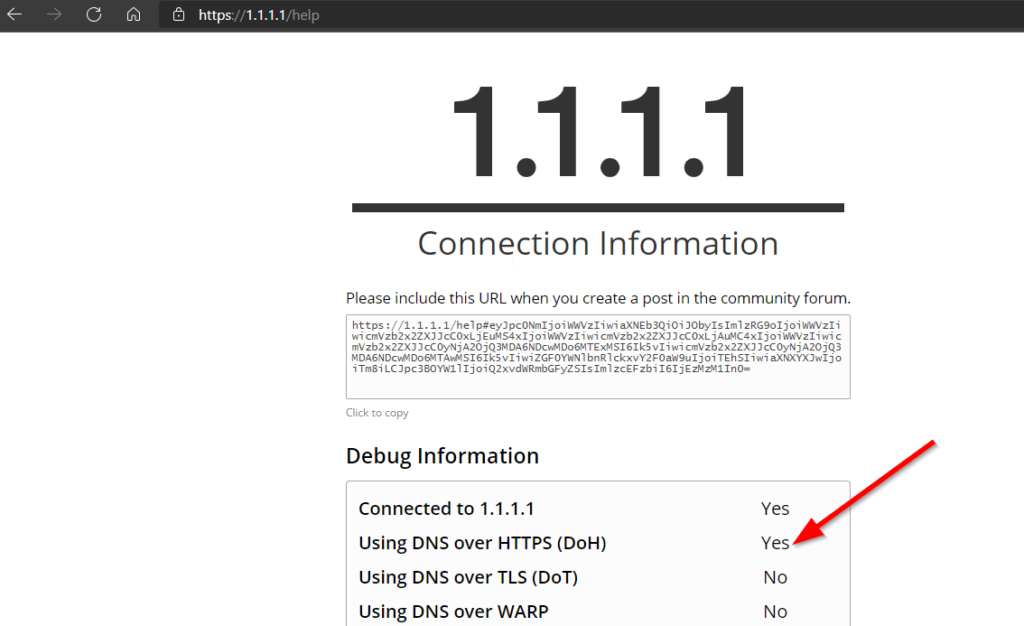
Another way you can test if DNS over HTTPS is enabled on your browser and working is by visiting the web address https://1.1.1.1/help on the browser you want to test. You can click on this 1.1.1.1 — the Internet’s Fastest, Privacy-First DNS Resolver if you are reading in a browser. The result will appear as shown below.
How to Enable DNS Over HTTPS in Chrome, Firefox, and Edge Browser
Chrome Mobile
The latest versions of Chrome browsers now have the DNS over HTTPS feature in the mobile app. To enable it, you can follow the steps below;
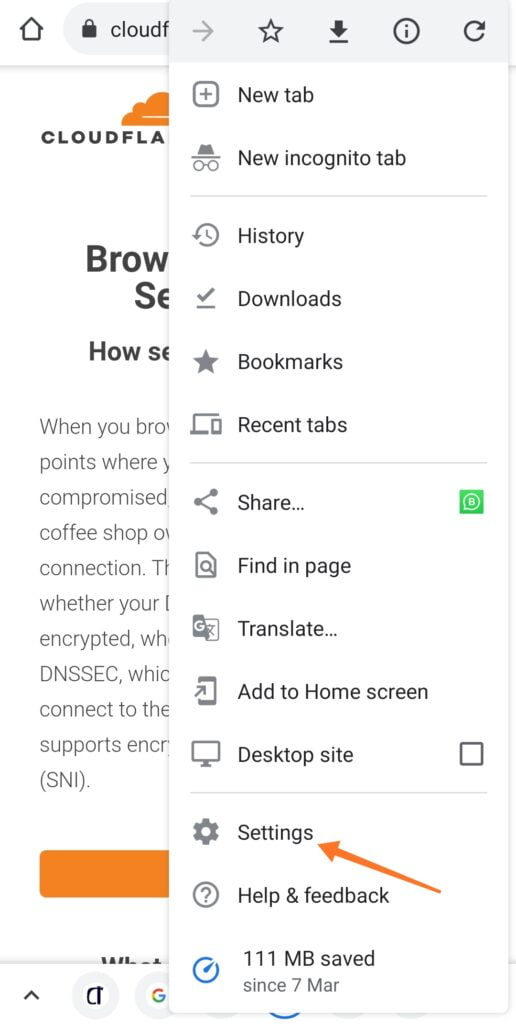
1. Go Settings: Select the three vertical dots by the top right to launch the browser menu as shown below. Then tap on Settings.
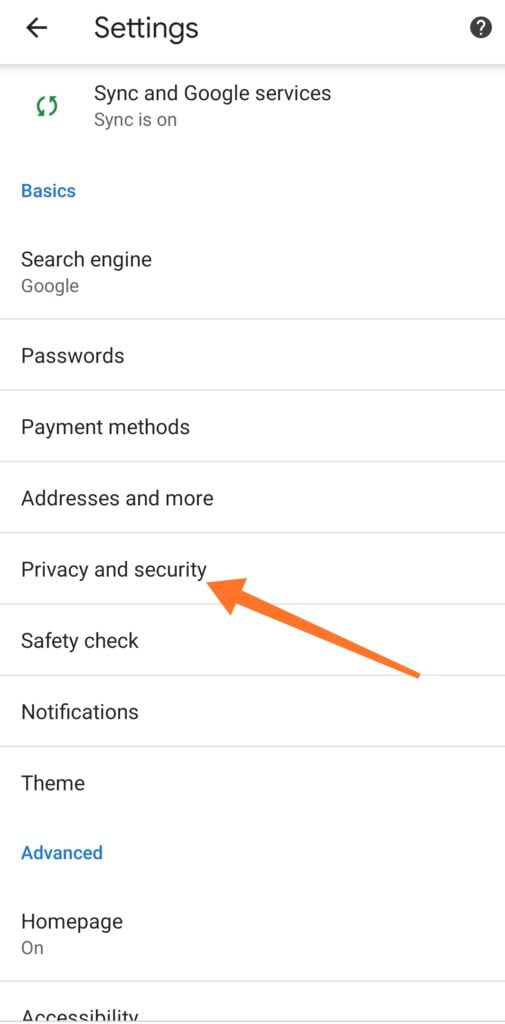
2. Scroll down to select Privacy and Security.
3. Then scroll down again to Use Secure DNS and select it.
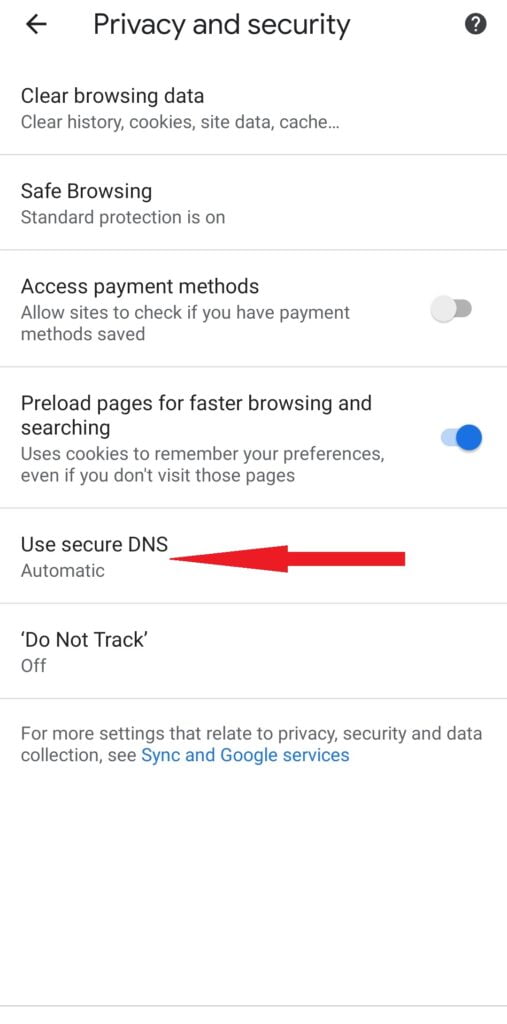
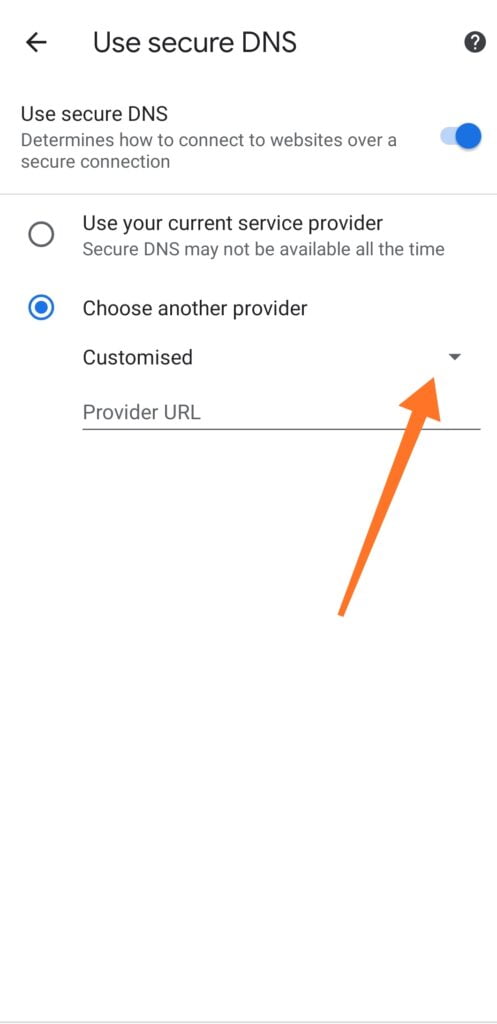
4 Check the Choose another provider radio button. Then tap on the little arrow down. After that, you can choose any provider you want and close the setting. You can choose Cloudflare if you want.
Chrome Desktop
For Chrome browsers on a computer, you can enable DoH using the following steps;
1. On the chrome browser address bar, type chrome://settings/security and press the Enter key on your keyboard.
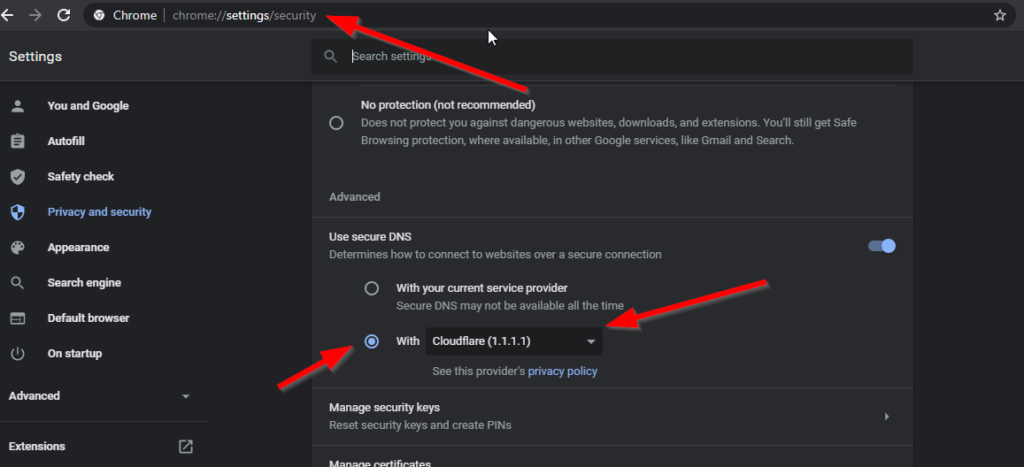
2. Scroll down until you see the Advanced section. Select the With radio button and then choose a DNS option. After that, close the settings.
Microsoft Edge
1.On the Edge browser address bar, type edge://settings/privacy and press Enter key on your keyboard.
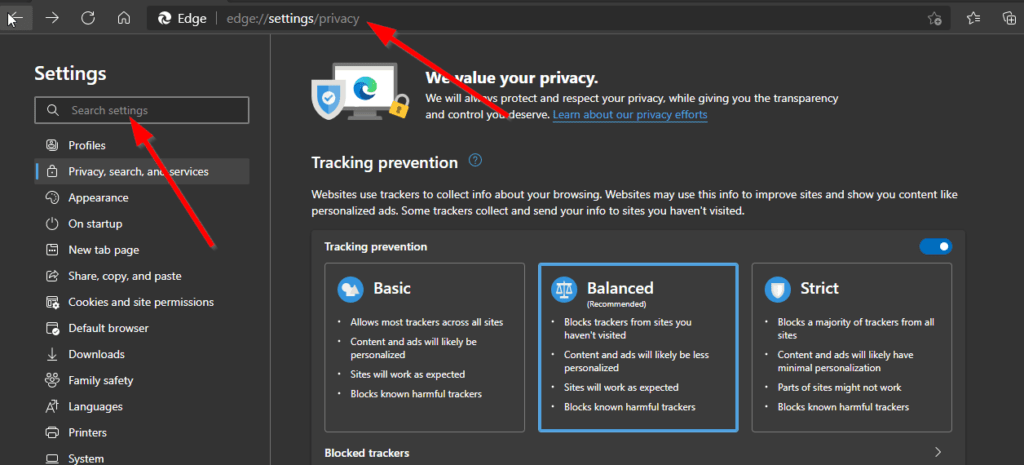
2. Scroll down until you see the option to use secure DNS, or in the search settings box by the top left, type in “DNS” to display the secure DNS setting will appear.
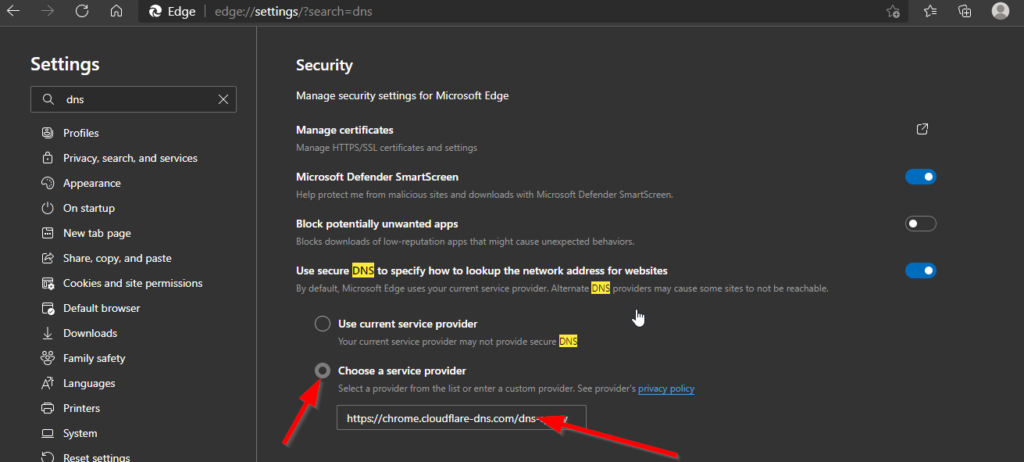
3. Select the Choose a service provider radio button and choose a provider from the selection box. Make sure you verify the provider if the verify check box appears by checking it. Then close the setting.
Firefox
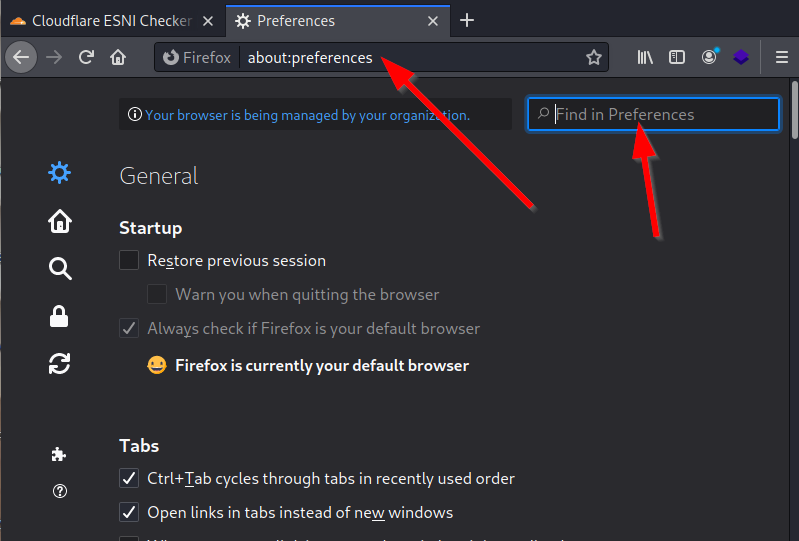
1. On the Firefox browser address bar, type about:preferences and then press the Enter key on your keyboard.
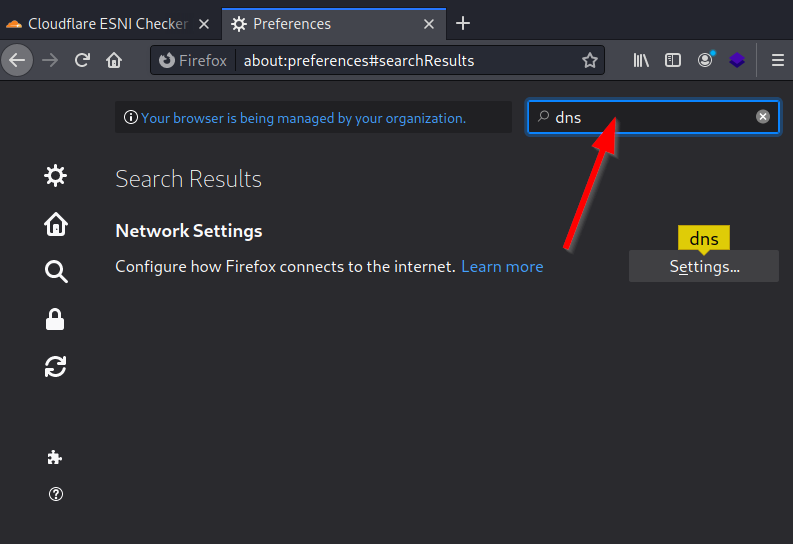
2. By the top right, type in “DNS” on the Find in the Preferences search box. Then the Network settings will appear.
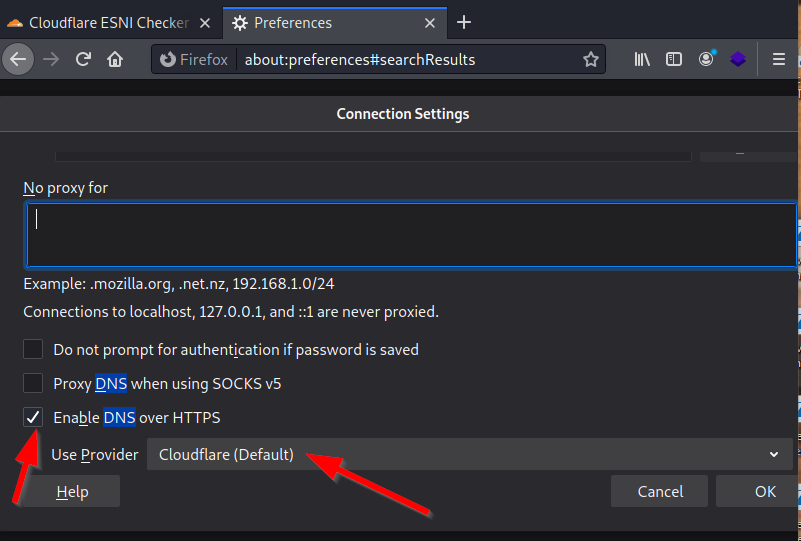
3. Click on Settings, then scroll down until you see the Enables DNS over the HTTPS check box. Select the checkbox and choose a secure DNS provider. Then click ok.
Opera
1. Click on the Opera icon to open the browser’s menu.
2. Select Settings from the menu or press Alt + P shortcut on your keyboard to open Settings directly.
3. Click on Advanced and then select Browser on the left.
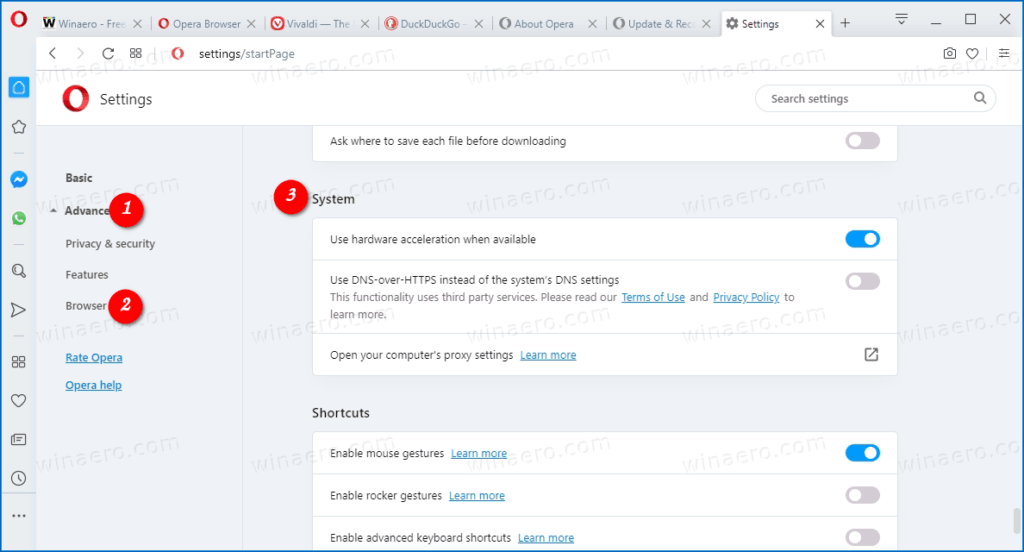
4. On the right pane, scroll down until you get to the System section.
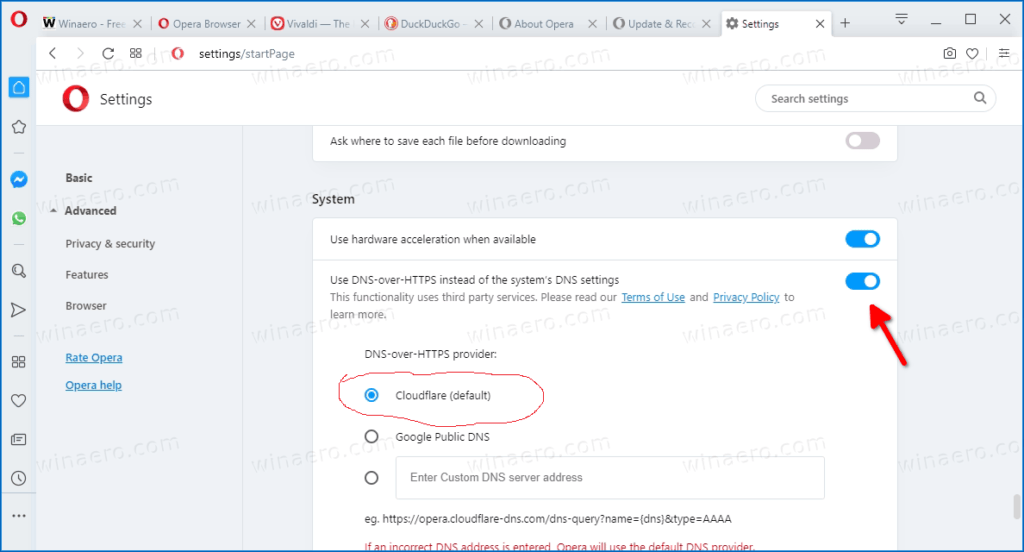
5. Toggle on the option Use DNS-over-HTTPS instead of the system’s DNS settings and choose a provider. Cloudflare is always the default and you can go with that.
Is it a good idea to turn on secure DNS or DoH?
The answer is yes for personal use, as this will add additional layer of security and privacy benefits to your browsing experience.
It is not advisable to allow the use of DoH in an enterprise environment, as this will make it difficult to carry out domain restrictions of employees.
DoH is also not allowed to be turned on in a browser that has parental controls enabled.
Suggested Post: Internet Privacy and Anonymity-Tools To Use
Remember, that you are told that it is private does mean you are invincible. Your ISP may still be able to track the site you visited if the IP was not encrypted.