Don’t Make This USB Charging Mistake; Hackers Use It to Hijack Your Phone
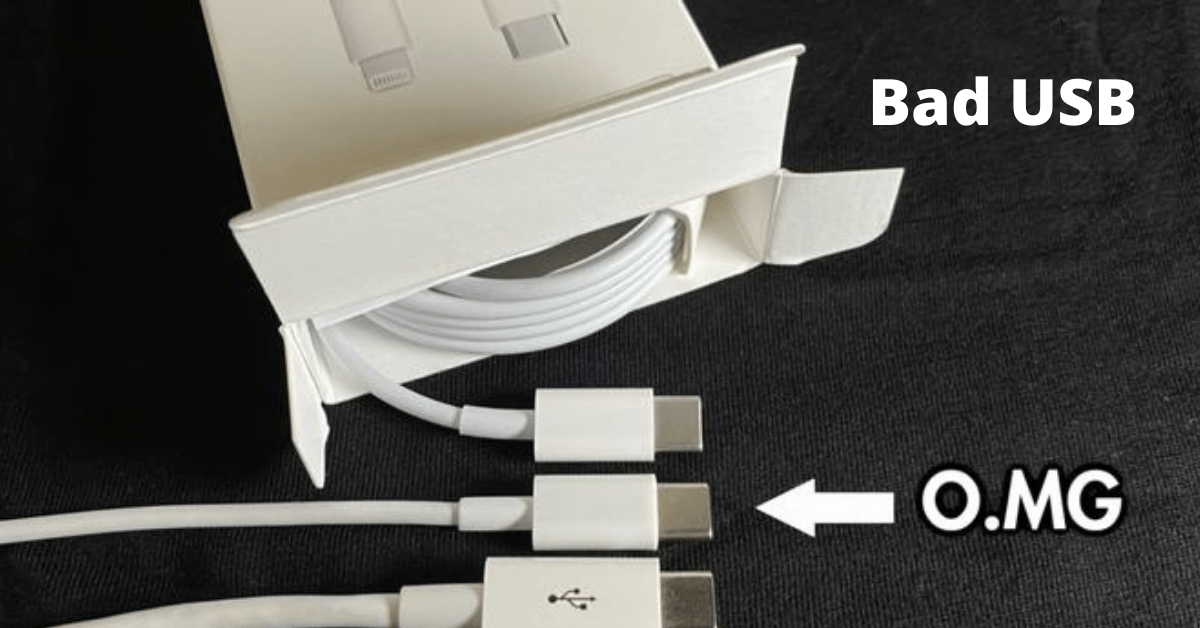
Have you heard about OMG cable before? When last did you borrow a USB charger from people to charge your phone?
Tips about cybersecurity or internet security, internet fraud or scam, and hacking. Learn more about cybersecurity and how to protect yourself from online scammers.

Have you heard about OMG cable before? When last did you borrow a USB charger from people to charge your phone?

Using the internet without having these cybersecurity secrets at your fingertips makes you more vulnerable to cyberattacks. The internet is now becoming very inevitable for all. If you are not using it to communicate, you may be using it for…

Creating fake websites is easier today than it was before. Even though fake websites are very easy to create these days, it is also very difficult to detect once created.

Wi-Fi is a technology many use for their everyday activities. Like every other technology; it is not immune to security vulnerabilities by default.

With the advent of malicious and phishing links, it is now common cybersecurity advice to tell people to avoid clicking on links.

A greater number of relationships are going to start on social media in the near future.

With the surge in the price of Bitcoin, the desire to invest in cryptocurrency has increased for many.

There is a possibility that someone somewhere is monitoring you on your phone using spyware.

Having online accounts has become a necessity in the world we are living in today. Whether it is a social media account, an internet banking account, or whatever accounts, the need to protect it from unauthorized users can not be overemphasized.

Recovering a hacked Facebook account after the hacker has changed your email and phone number is difficult but very possible.
you're currently offline