Most people detect that their windows computer is hacked only when they are denied access to their computer or blocked in their online accounts. But the question is, will you always get kicked out of your computer or online accounts whenever you get hacked?
The answer is no. This is because a hacker can start stealing useful data from your computer remotely without your notice.
Most times, you may not have noticed the day you granted the hacker access to your computer. It may be that day you were roaming the internet looking for where to download a free app, pdf, or other files. That might be when you ended up downloading a pdf file or an app that has backdoor payloads in them.
A simple act of opening a pdf or Microsoft document to check if it was what you wanted to download is enough to sell out your system to a hacker remotely. Especially when you don’t have an updated computer antivirus running.
Therefore, before you start wondering why money was moved from your bank account without you giving out your banking details, make sure you read this post. The person hacking you might be dwelling in your computer already and having remote access. Read on to learn how to detect and prevent such.
Suggested Post: One Way Text Messages Are Hacked In An Android Phone
How To Check If Your Windows Computer is Hacked Already Or Not
How do you know that your system has been compromised even when the hacker has not kicked you out of your computer?
There is no one answer to this question. But I will show you two common ways you can check on your system to ascertain if you are safe or not.
1. Using Windows Computer TCPView Application
TCPView is a small size Windows computer program that will show you detailed listings of all TCP and UDP endpoints on your system, including the local and remote addresses and state of TCP connections. You can download it by clicking HERE. After downloading it, extract the zip file and simply click one of the files named tcpview or tcpview64 depending on your system processor.
Without using many technical terms. One important thing you should note is that before your computer gets information from the internet or another computer; it must establish a connection with the source computer. When such a connection is established, then it is now possible for both computers to exchange data.
Every computer has two standard ways of establishing connections to one another on the internet; It is either through TCP/IP or UDP. TCP is the most common type of connection that makes sure the two computers are connected before the transmission of data. UDP on the other hand is a type of connection that transmits data without confirming the connection. An example is video streaming.
You might be wondering, how is this going to help me detect hackers on my windows computer. The fact is that hackers take advantage of these connection types to create what is called reverse TCP/IP or bind connection between you and their system in order to steal data and information from your system remotely.
Using a simple application like Netcat, it is possible for a hacker to create a remote connection to your computer and use it to spy and steal data from your system without your notice.
Therefore, what TCPView is going to do for you is to help list all the established, listening, closed and time_waiting connections between your windows computer and other computers.
How To Analyze The TCPView Result On Your Windows Computer
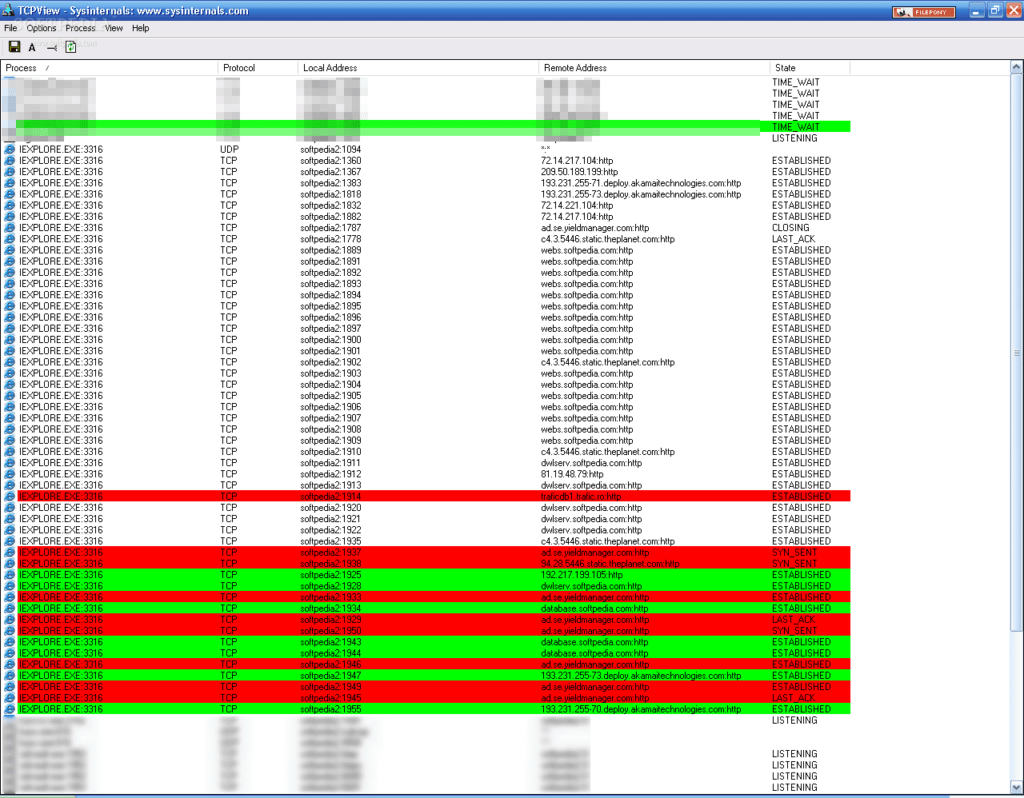
TCPView displays all the programs on your computer that are currently connected to a remote computer over the network or listening for incoming connections. The program details are divided into 5 columns that provide useful information about them.
The Five Columns and What They Stand For
Process: This shows the names of running programs or applications that are installed on your Windows computer and is running.
PID: This shows the process ID for the particular programs.
Protocol: The protocol column tells you whether the particular program is using TCP or UDP.
Local Address: This lists the hostname or IP address of your own computer’s connection.
Local Port: This column will show the port number being used by the programs on your windows computer. If the port number corresponds to a standard service, it will show the service name instead.
Remote Address: This is the IP address or hostname of any remote device your computer program is connected to.
Remote Port: This column will show the port number being used by the remote connection. If the port number corresponds to a standard service, it will show the service name instead.
State: This column shows the state of the program’s connection. These states are:
Established – A connection that is established means that there are is an active connection between your computer and the remote computer.
Close Wait – The remote connection has closed the connection. This entry will eventually time out and be removed from the TCPView list.
Time Wait – Your computer has closed the connection. This entry will eventually time out and be removed from the TCPView list.
Listening – This state means that the program is listening for an incoming connection from a remote computer. The port that it is listening on can be found in the local address column.
How To Analyze TCPView Result:
To analyze the TCPView to see if your computer is hacked, you will have to observe the process name of all the connection that is established or is listening on your computer. Check if the process name is familiar. Whenever you see a process name that is not familiar to you, the best thing to do is to google about it and what it does. With that, you can know whether they should be on your computer or not.
The reason why you should be conscious of the process name is that hackers install a backdoored applications on your system after gaining access in order to maintain access. The app enables the hacker to main an open port on your computer for easy reconnection and access.
You will also need to observe the remote address, to know exactly where your computer is connecting to.
Once you see any strange process running; right-click on it; view the properties to see the path where it is saved on your computer. Checking the path is very important as hackers do save their own app using a name similar to common apps. Then uninstall or delete it or right-click and kill the process.
Related Post: How to Block Apps From Stealing Your Personal Data From Your Android Phone.
2. Using The Task Manager
The task manager is an application on your windows system that gives you information about your system performance, running software, names of running processes, logged-in users, windows service, etc. Before you can use the task manager, you will first have to load the application on your windows computer.
Related Post: How to Know If You Have Been Hacked
There are so many ways you can open the task manager. You can go straight to your Start button; type in “task manager” on the search box. Then click on it to load it when it appears on the search result.
Also, you can press the ctrl + shift + Esc key together on your keyboard to load it; or press windows + x on your keyboard and select task manager on the list of menus that will appear.
How To Use Task Manager To Detect If Your Windows Computer Has Been Hacked
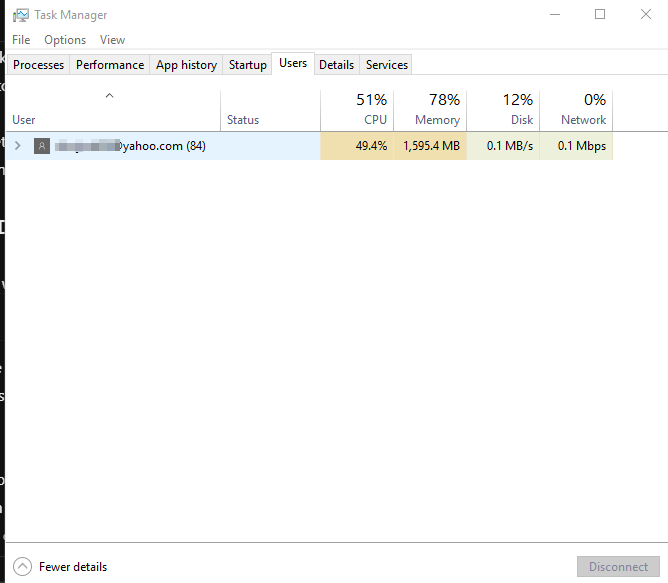
Once you have loaded the task manager, you will see seven tabs; Processes, Performance, App History, Startup, Users, Details, Services tab. When you click on each of these tabs, their different details will appear below them.
When you open the task manager app, it is important you do this first. Click on the View option in the menu bar at the top and make sure that Group by type option is ticked. If not, click on it to tick it. This will help separate your processes into different groups of types Apps (shows apps you downloaded), Background(shows apps running in the background), and Windows processes (shows system apps running).
To start checking if you have been hacked; Firstly, click the Users tab, you will see the list of users on your computer. If you see a username you can’t remember creating; that means someone is using your system at your back.
Remember, the task manager is not a place to come and exhibit your computer hacking skills without understanding what you are doing. You might end up ending a task that might shut down your system while you are still trying to do something.
What do you do now if that is the case? How else do you know if your system is hacked?
First, you should look at your App process group. Check if it is only the processes of Apps you are working with and is open that is running.
If you see any app process that is running and you can’t see the app on your taskbar, then you have to verify it. You can verify by googling the process name, to see if it is an app you use.
Suggested Post: How You Get Hacked- Basic Cybersecurity
To end a task; simply select the process by clicking on it. Then look at the bottom of the window and click on End task. Or you can right-click on the process and a menu list will appear, then select End task. Your job here is just to fish out anything suspicious and end the task.
Note: Always remember to google the name of a process if you are confused about what it does before you end the task. Not only that but also make sure you check the path where the app file is saved. Sometimes, hackers save malicious apps with names similar to the system app.








Hi nice website