Have you heard about the latest sextortion scam? If you have not, then make sure you read this post till the end. Even if you have heard about the term before, keep reading, as we will explore possible ways people fall victim to this killer scam and how you can avoid it.
Is someone threatening to share your nude picture online? Have you sent your nude to someone on social media before? Or do you engage in sexting or watch porn online?
In the world we are in today, the barrier to what will harm us or embarrass us has been broken. We don’t have to step out of our houses anymore before we can get into trouble or get embarrassed. Troubles are staring us in the face each time we lift our mobile devices. Once you own one, automatically, you have acquired for yourself two enemies: those that will hate you for not reaching out to them as often as they expected you to and those that will hate you because of what you said when you reached out to them.
The same thing applies to the internet and social media, so far as you use any of them; you should understand that you are no longer far from being embarrassed or reached by the enemy. Every parent should make their kids understand that.
What are sextortion and sextortion scams?
Sextortion is someone threatening to distribute your private and sensitive materials if you do not provide for their demand, which might include money or sexual favors.
Sextortion scam is the act of blackmailing people by claiming to have their nude pictures or information about their sexual acts. In other words, it is the act of someone claiming to have your naked pictures with them or information about your cheating act for married couples and threatening to share them online if you do not comply with their demand.
Two Kinds of Sextortion Scam
For more clarity, I have decided to categorize sextortion scams into two broad categories:
- Sextortion scams based on a claim
- Sextortion Scam based on real, nude pictures
We are going to take them one after the other and analyze how the bad actors perpetrated them, what makes them successful, and how you can handle the situation.
Sextortion Scam Based on a Claim
This kind of sextortion scam is orchestrated using social engineering. In this kind of sextortion scam, the bad actor does not have nude images of their target victim with them, but they are only trying to use psychology to make their target believe they do.
This is a situation where the target receives an email, phone call, or text message from a stranger claiming to have hacked into their computer or phone and stolen their nude pictures. They may also claim to have information about the target’s secret chats, social media, and contacts.
For the scammers to make their victims believe their claim, they usually have to prove to them that they have the capacity or capability to hack or to have hacked their computer or phone. And with respect to that, they also claim that they have in one way or another installed what they can use to monitor their target through their device camera.
The scammers most often support their capability claim to hack their victim by using phrases like “I am a member of an international hacking organization” or “a company that engages in cybersecurity services” in their conversation with their target.
For them to make their claims more believable, they will have to look for common situations where people’s nude can be gotten or things people are prone to may have done and include them as the source for the nude picture they have.
Three of the most common situations or scenarios they mostly use as their source are that they got their target nudes while they were watching porn, sexting on social media, through a hotel camera, or through images stored on their target’s computer or phone.
Once they get their targets to believe them, the next step is to include some sense of urgency in their message or email. This is done by asking their target to do what they want in the next 24 hours or 30 minutes so they won’t leak the pictures online.
Below are examples of sextortion emails:
“For a while I am watching u thru camera, and you never cease surprising me.
I fear to suggest how you got such great affection for jack off, and ur habits are a nightmare…
To be honest, i find nothing bad in masturbation, it isn’t for me to condemn you.
Another question is if your pleasure oneself was shot via ur camera, then that changes everything. I recorded your jerk off using the camera of your device, and now I have a very entertaining video tape u are in.
Thru remote access I have downloaded contact information from your mail and social network. Now you see why I’m telling all that? I’m going to distribute it among ur relatives and post it on the web.
You pay me, only then I will delete all dirty laundry in relation to u and leave u in peace, saving your public image in the eyes of others.
You have forty-eight h to give money to me as soon as you open the text, I will be notified when u read it.
If u flout my requirement, in 96 hours the take where you jack off is gonna become the world heritatage on the net.
it’s your choice whether u care about your prestige. And stop browsing questionable websites, since ur device may be infected even if there’s installed anti virus.”
The above kind of email might have your email address both as the sender and receiver address. You can verify the email header if you can do it safely, but never download files, reply to the email, or click any link associated with the email.
Below is another example of an email targeting married spouse:
“[Spouse name] is cheating on you.
Here a proof.
As a company engaged in cyber security we’ve found information to [Spouse’s name] that interest you.
We made a full backup of his disk ( We have all his address book, social media, history of viewing sites, dating apps, all files, phone numbers, and addresses of all his contacts) and are willing to give you full access to this data. For more details visit our website.”
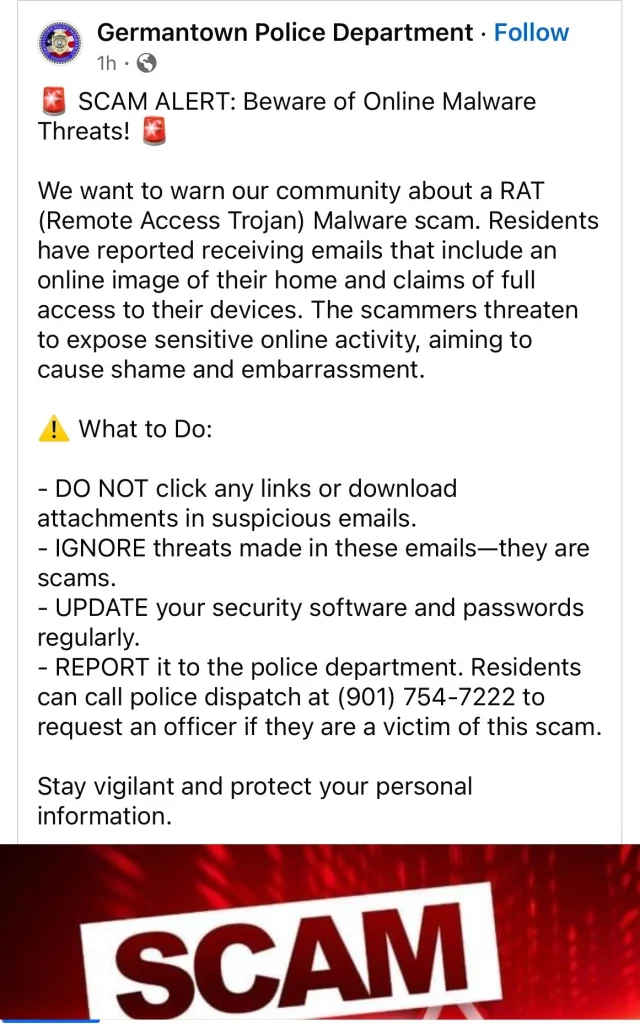
These kinds of scams happen to those who had been victims of data breaches and the scammer will on most occasions, mention your real name. They might as well send you an image of your home and claim access to your home devices.
Contact us if you need help with a sextortion situation
Why is This Kind of Sextortion Scam Successful?
One thing that makes a sextortion scam based on a claim successful is that the bad actors harness the idea of people’s commonality of character in crafting their message.
They knew that out of ten people owning an internet-enabled smartphone or computer, at least one out of the ten watch porn on their device, sex chat with their partner or someone else on social media, suspect their partner is cheating, or may have knowingly or unknowingly saved their nude on their phone or computer.
Therefore, the scammer gambling on those ideas has a high probability of them catching a victim that is unaware of the scam.
The second reason that makes this kind of sextortion successful is the target’s knowledge that they can be hacked and their ignorance of how exactly or how to check if they have been truly hacked.
The scammer rides on this target ignorance by placing themselves on high status by saying they belong to a well-recognized hacker group or a cybersecurity company.
Also, the fact that the attacker may have genuine leaked information about their target makes it possible for them to send an email mentioning the correct names of their target and even names they are not popularly known with.
How to Handle Sextortion Scam That Are Based On Claim
The fact is that you are not the target of this kind of scam until you reply to the scammer’s message, phone call, or email, or even click the link or download the file attached to the email.
This is because sextortion scammers send out the same message you received to many people at the same time, and they are simply waiting for someone to get caught on the web.
Your reply proves to them that you are a victim of the situation they described in their message, and that strengthens their target at you.
There are rare cases where the message is solely targeted at one target, which is known as spearphishing, but the situation is always similar. If you don’t reply, then you are no longer a worthy target.
Therefore, the best way to handle this kind of sextortion scam is to ignore the message and report it to appropriate authorities or share the information for others to learn. You can save the message, but never try to reply to the message or give a callback if it was through a phone call.
In a situation where you have responded to their message, the best way to be out is simply to stop meeting their demand, except if you have placed yourself in the second category, which we will be discussing next.
Sextortion Scam Based on Real Nudes
This is the type of sextortion scam where you voluntarily or involuntarily send your nude picture to the scammer. This kind of scam may sometimes come from people we know, not just scammers.
Why is This Kind of Sextortion Scam Successful?
What makes this kind of sextortion successful is the victim’s fear of being embarrassed, exposed, or of what will happen if people find out. This fear is always heavy on people who are into marriage, have some kind of public recognition, or are dependents. Scammers bank on these fears to actualize their demands from the victim.
How to Handle Sextortion Scam Based On Real Nudes Pictures
One thing you should understand is that sextortion is a crime. So, the scammer or the person scamming you is committing a crime, not you, and you should not feel embarrassed to report them.
Therefore, the best way for you to handle that is to report them to the appropriate authorities. This is very important if you are a dependent or a teenager.
The second way you can handle it is by ignoring them. Though not the same way you handle sextortion based on a claim, in this case, you will have to ignore them and still monitor online to see if the scammer is truly circulating the nude pictures as they have threatened.
You can check that using reverse image search on websites like TinyEye and Google image search. If you find the image online, you can reach out to the platform where it was distributed for removal or report it to the authorities to help you achieve that and capture the perpetrator.
Another way you can remove the images if they are shared is by creating a case on stopncii.org submitting the image the scammer is threatening to expose on the platform. StopNcii will help you remove the image from every social media platform they partner with, with which the scammer may likely share the nude picture.
The third way is denial. This may not be the most effective, but with the era of AI and photoshopping, you can make a case that you are not the one in the pictures. The bottom line is that you should avoid anything that will make you start yielding to the scammer’s demands.
Who Are the Most Vulnerable to Sextortion Scam?
Everyone using the internet is vulnerable to sextortion, but those who are more likely to fall victim to the scam are mostly married people who visit porn sites or sext online and teenagers who sext on social media. That is because they are the most likely to respond when targeted by these scammers, and they are always more eager to fulfill the scammers’ demands.
There are cases of people committing suicide because of sextortion scams, so please share this post to help save lives. If you feel that your computer or phone has been hacked, you can contact us to help you verify the incident.
As a teenager, irrespective of how your sex drive pushes you, do not make the mistake of sending your nude pictures to someone through social media. This applies to people you know. If your boyfriend or girlfriend wants to see your nakedness, they should come physically. Using social media to fulfill the demand will end up putting you at risk of sextortion.




