Ransomware has emerged as one of the most pervasive and damaging cyber threats in recent years. Its consequences can be devastating, affecting individuals, businesses, and even critical infrastructure.
Whenever ransomware is mentioned, many tend to focus on the highly notable reported cases like the WannaCry (2017): A global ransomware attack that affected over 200,000 computers in 150 countries, causing billions in damages; Colonial Pipeline (2021): A ransomware attack that led to the shutdown of a major US fuel pipeline, causing widespread fuel shortages; or JBS Foods (2021): A ransomware attack on one of the world’s largest meat processing companies, disrupting food supply chains.
It will surprise you to know that only few of all the ransomware attacks that happen are reported. This may be due to the victim’s fear of reputation damage, financial loss due to legal consequences, insurance premium, reluctance to involve law enforcement or regulatory bodies, or lack of awareness or understanding of reporting requirements.
In that case, 57% of ransom attacks go unreported (Source: Cybersecurity Ventures), and 70% of organizations don’t report ransomware attacks ( Source: Ponemon Insitute). Also, only 1 in 5 ransomware attacks are reported to authorities (source: Europol), and 60% of small and medium-sized businesses (SMBs) don’t report ransom attacks (source: Datto).
In this post, we will explore effective strategies to protect yourself and your organization from this growing threat and how to respond when it happens.
What is ransomware?
Ransomware is a type of malicious software—or malware—that prevents you from accessing your computer files, systems, or networks and demands you pay a ransom for their return.
There are several types of ransomware, including:
1. Crypto Ransomware: Encrypts files and demands payment for the decryption key.
2. Locker Ransomware: Locks the victim out of their device entirely.
3. Double Extortion: Threatens to release stolen data if the ransom is not paid.
Contact Us Today for Your Cybersecurity Needs
How Ransomware Works
Attacks using ransomware are becoming more sophisticated and prevalent. Gaining knowledge of the three main phases of an attack with ransomware will enable you to better safeguard your data and infrastructure. Below are the three main phases:
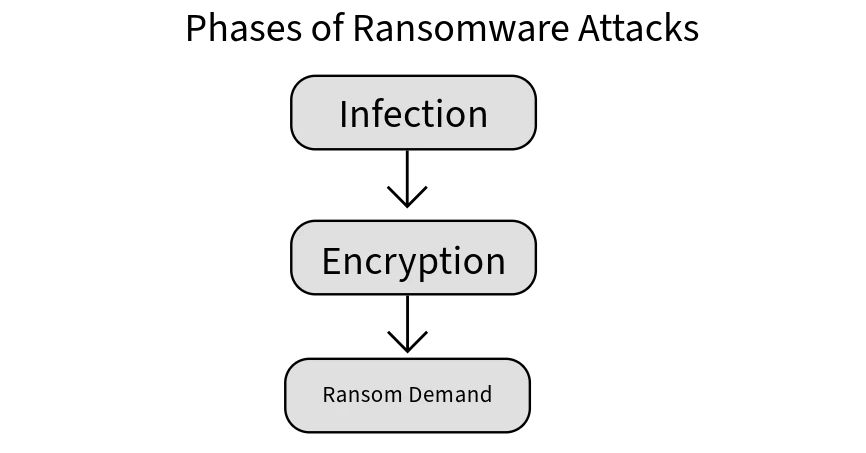
1. Infection: Ransomware often obtains initial access through mass phishing and spear-phishing emails, malicious attachments, compromised websites, or exploiting public-facing applications through known vulnerabilities to obtain initial access.
The following exploits based on the following CVEs have been observed to have been exploited by some ransomware group: CVE-2023-3519 (CWE-94) , CVE-2023-27997 (CWE-787 | CWE-122) , CVE-2023-46604 (CWE-502) , CVE-2023-22515 , CVE-2023-46747 (CWE-306 | CWE-288), CVE-2023-48788 (CWE-89), CVE-2017-0144 , CVE-2020-1472 , and CVE-2020-0787. (Source: CISA)
The initial access happens once the victim clicks on a malicious link or downloads an infected file; the ransomware is installed on their device. There have also been cases where initial access was gotten using RDP tools.
CISA Joint Cybersecurity Advisory listed the following IP addresses for Known IPs Related to Malicious Activity (2023-2024). Remember to very these IPs before blocking them in your environment.
| IP Address |
| 8.211.2[.]97 |
| 45.95.67[.]41 |
| 45.134.140[.]69 |
| 45.135.232[.]2 |
| 89.23.96[.]203 |
| 188.34.188[.]7 |
| 193.106.175[.]107 |
| 193.124.125[.]78 |
| 193.233.254[.]21 |
2. Encryption: The ransomware encrypts the victim’s files, making them inaccessible. The attacker may also steal sensitive data during this process.
3. Ransom Demand: The victim receives a ransom note, usually displayed on their screen or printed through network printers, demanding payment in exchange for the decryption key. The note often includes instructions on how to pay the ransom, typically in cryptocurrency.
The Impact of Ransomware
Ransomware attacks can have severe consequences, including:
Financial Loss: Victims may face significant financial losses due to ransom payments, downtime, and recovery costs.
Data Loss: If the ransom is not paid, victims may permanently lose access to their data.
Reputation Damage: Organizations may suffer reputational damage, leading to loss of customer trust and business opportunities.
Operational Disruption: Critical services and operations can be disrupted, affecting everything from healthcare to transportation.
Actions to take in order to mitigate cyber threats from ransomware
Below are lists of actions you can take today as an organization, business, or an individual to reduce cyber threats from ransomware:
- Backup and recovery plan: Ensure sensitive data is backed up in multiple locations (e.g., hard drive, cloud) that are separate and secure.
- Password management: Follow NIST standards:
- Use passwords with 8-64 characters.
- Store passwords in hashed format with a password manager.
- Add “salts” (random data) to shared credentials.
- Don’t reuse passwords.
- Lock accounts after several failed login attempts.
- Disable password hints.
- Change passwords only once a year unless necessary.
- Admin credentials should be required to install software.
- Keep systems updated: Regularly update operating systems, software, and firmware. Prioritize patching known vulnerabilities, especially in internet-facing systems.
- Multifactor authentication (MFA): Require phishing-resistant MFA for admin accounts and standard MFA for other critical services. Security keys like Yubikey Security Key is a good option.
- Network segmentation: Control traffic between networks to prevent ransomware spread.
- Monitoring and detection tools: Use tools that monitor network activity and detect abnormal behaviors (e.g., Endpoint Detection and Response – EDR).
- Antivirus software: Install, update, and enable real-time antivirus detection on all devices.
- Logging best practices: Use secure logging methods and review logs regularly to detect suspicious activity.
- Access control: Audit and limit admin privileges following the principle of least privilege.
- Disable unused ports: Turn off any unnecessary network ports.
- Email security: Implement strict email security policies, disable macros and hyperlinks in emails, and add banners to emails from external sources.
- Time-based admin access: Use Just-in-Time (JIT) access to limit admin rights to only when needed.
- Command-line and scripting restrictions: Disable command-line tools that attackers may use to escalate privileges or move within the network.
- Offline backups: Keep backups offline, ensure they’re encrypted, and regularly test restoration processes.
- Test your defenses: Regularly test your security tools against known cyberattack techniques (such as those in MITRE ATT&CK) to evaluate their effectiveness. Tune your security systems based on these results to improve protection.
How to respond when hit by ransomware attack
Even though ransomware attacks can be extremely damaging, there are things you can do to lessen the harm and get better. They are broken down into four stages below;
1. Detection and Analysis
- Identify and isolate impacted systems: Immediately disconnect affected systems from the network. If several systems are infected, consider taking the entire network offline.
- Prioritize critical systems: Focus on isolating essential systems first.
- Use out-of-band communication: Avoid alerting attackers by communicating through phone calls instead of emails or online platforms.
- Power down devices if needed: Only do this if disconnecting them is impossible, though you may lose critical evidence.
- Investigate and triage: Look for signs of the initial attack using antivirus or other monitoring tools. Malware like Emotet or QakBot may be involved.
- Document and analyze: Work with your team to understand the situation and begin threat hunting.
2. Reporting and Notification
- Notify key stakeholders: Inform your IT team, cybersecurity partners, and top management. Coordinate with public information personnel if necessary.
- Report to authorities: Contact CISA, the FBI, or local law enforcement agencies to seek assistance.
In the USA Report the compromise to CISA via CISA’s 24/7 Operations Center (report@cisa.gov or 888-282- 0870). State, local, tribal, or territorial government entities can also report to the Multi-State Information Sharing and Analysis Center (MS-ISAC) (SOC@cisecurity.org or 866-787-4722).
In the UK cyber security incidents can be reported to the NCSC by visiting https://report.ncsc.gov.uk/.
In Nigeria, ransomware attacks can be reported to the Nigeria Police Force’s (NPF) National Cybercrime Centre (NPF-NCCC) through their reporting platform: https://nccc.npf.gov.ng/ereport/signin .
In Canada If you experience a ransomware attack, report it to the Canadian Centre for Cyber Security through My Cyber Portal or email contact@cyber.gc.ca.
3. Containment and Eradication
- Collect forensic evidence: Take a system image and gather any relevant logs for further investigation.
- Consult law enforcement: They may provide decryptors or tools to help with the ransomware.
- Identify affected systems and kill ransomware: Stop ransomware processes and isolate compromised accounts and systems.
- Analyze the attack: Investigate how the attackers gained access and remove their tools from the system.
- Rebuild systems: Focus on restoring critical services first and rebuild systems using secure methods, such as pre-configured images.
4. Recovery and Post-Incident Activity
- Reconnect clean systems: Restore systems from clean, offline backups, ensuring the malware doesn’t spread again.
- Document lessons learned: After the incident, update policies and procedures to prevent future attacks. Consider sharing what you’ve learned with others.






