Phishing email is one common way bad actors deliver their hacking tricks and weapons to capture their victims.
Attacks like ransomware attacks, credentials harvesting attacks, or business email compromise attacks are in one way or another delivered through a phishing email.
A phishing email is a fake or bogus email that doesn’t come from the sender it claims to come from.
For instance, when a cybercriminal creates and sends you an email that looks similar to the ones you normally receive from your bank or a company but is fake,
The success of a phishing email depends on how real or genuine the sender can make it look. This will make it easy for people to fall victim to the demands that come with such an email.
Below are some working tips that will help you recognize phishing emails when you receive them.
Ways to Recognize a Phishing Email
One thing that is ingrained in phishing emails is their demand for urgent action.
Whenever you receive an email that you did not request and it is asking you to click on a link, pay money to someone, download something, call someone, or solve urgent issues on your online account, you will need to check such an email to know if it is a phishing or scam email before you take those actions.
Below are the ways you can do that:
1. Verify the Sender Address
You cannot identify an email sender based on what you read in the email message body or subject.
That you saw the logo or name of a company you knew on the email messages doesn’t mean it is from them.
Because of this, it is important that you verify the email header by checking the “From:” and “Reply to:” options. This shows you where the email was sent from. Remember, the “reply to” email address should be the same as the “from address” in most genuine emails.
Depending on the email client you are using, you will see the email sender information before the main email message.
Remember, what you are looking for is to know if the email is coming from the claimed sender domain.
For example, if the email message claims it came from Amazon,. Then, the sender’s “From” address should look something like this: something@amazon.com.
If you see something@gmail.com or something@amazoN.com, it shows a phishing email.
What you check is the domain name after the @ sign or symbol in the email address.
Every known company should have a domain-dedicated email address. They will not be using free email domain services like @gmail.com or @yahoo.com, etc.
See the image below and the arrows on it. The email message claims it is from Norton, while the sender is not from Norton. This certifies it is a phishing email.
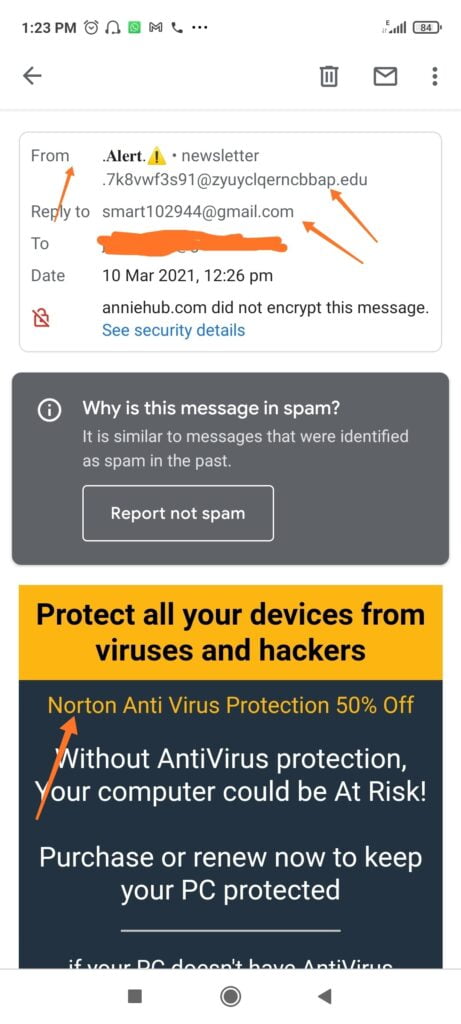
On some occasions, a phishing email might come using a company’s real email address, but it is not still from the company. The next way will help you recognize such emails.
Suggested Post: Internet Scammers Psychology- How to Unmask Them
2. Verify for Email Spoof
Bad actors sometimes use a spoofed email address for their phishing email scam.
Email spoofing is the process of forging another person’s email address and using it to send an email message.
Spoofing makes it possible for internet scammers to send you an email using the real email address of the company they want to trick you with their email.
In this case, verifying only the sender’s address won’t protect you. You will need to check if the sender’s email address can be spoofed and used by scammers.
To verify if an email address can be spoofed, you will need to trace the email with its full headers. There are different ways to copy the full email header, depending on the email client you are using.
For Gmail users:
1. Open your inbox in a browser.
2. Then select the email you want to check the headers for.
3. Next to Reply, click More > Show Original, or look for Show Original at the top of the email body.
Click on it and a new tab will open showing the email’s full header and source file.
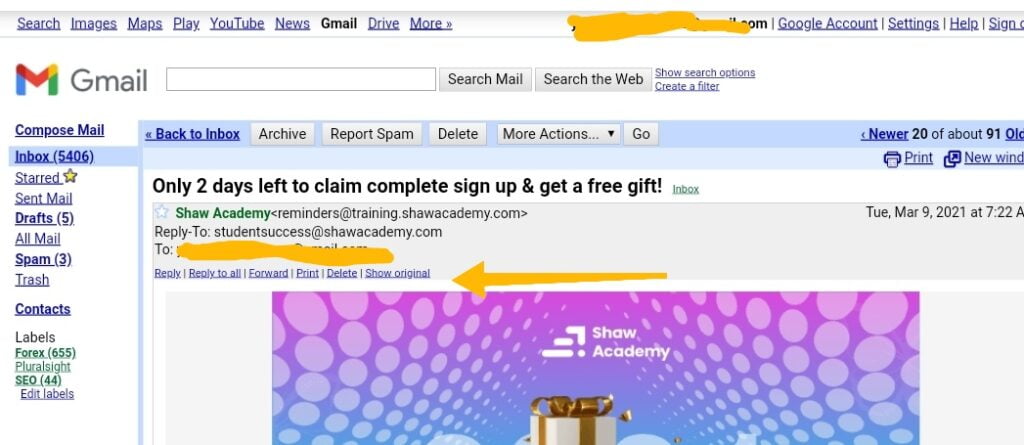
4. Then copy it and paste it into the Google header analyzer to analyse the header.
5. Check if the header passed SPF, DKIM, and DMARC authentication. If the result shows Pass for SPF and DKIM, it shows the email is protected from spoofing.
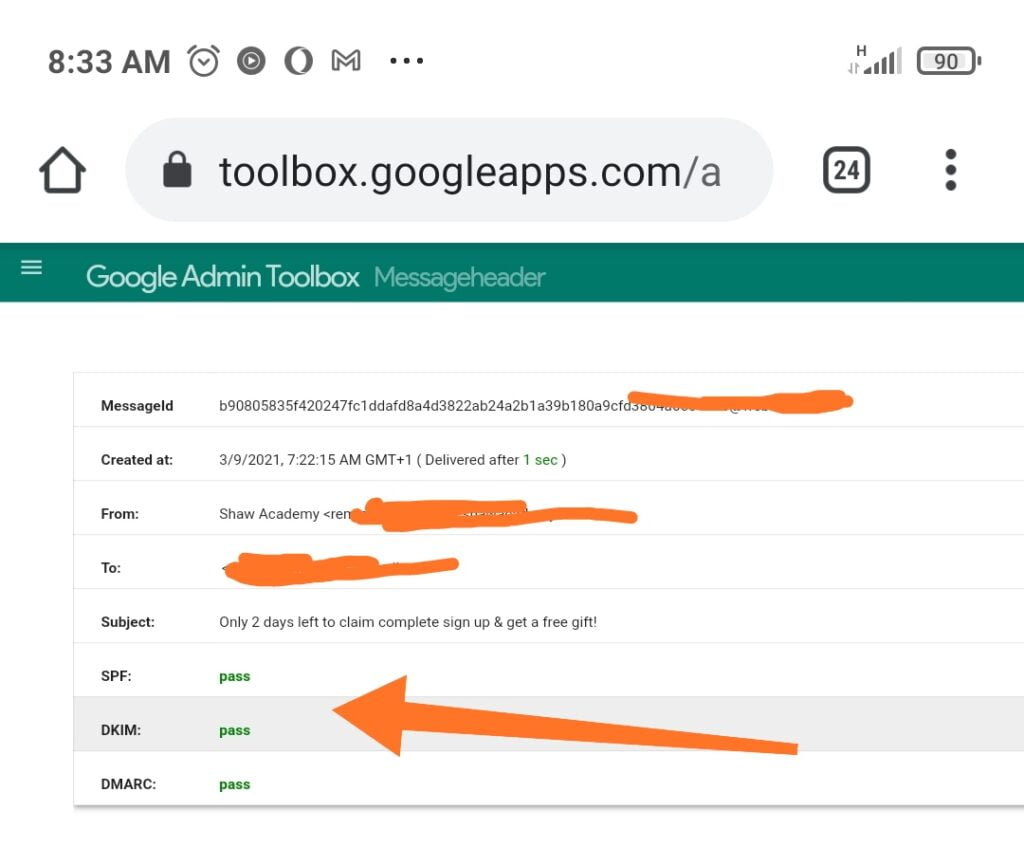
If the analyzer shows “hard fail” or “soft fail” results for SPF and DKIM, that means the email can be spoofed. Then, you should be careful about the particular email.
3. Check for Domain Name Homographic Attack Trick
The fact that some letters of the alphabet look similar when written together helps bad actors execute the IDN homographic attack.
In this attack, the scammer will like to change some alphabets to make it look like a genuine email address.
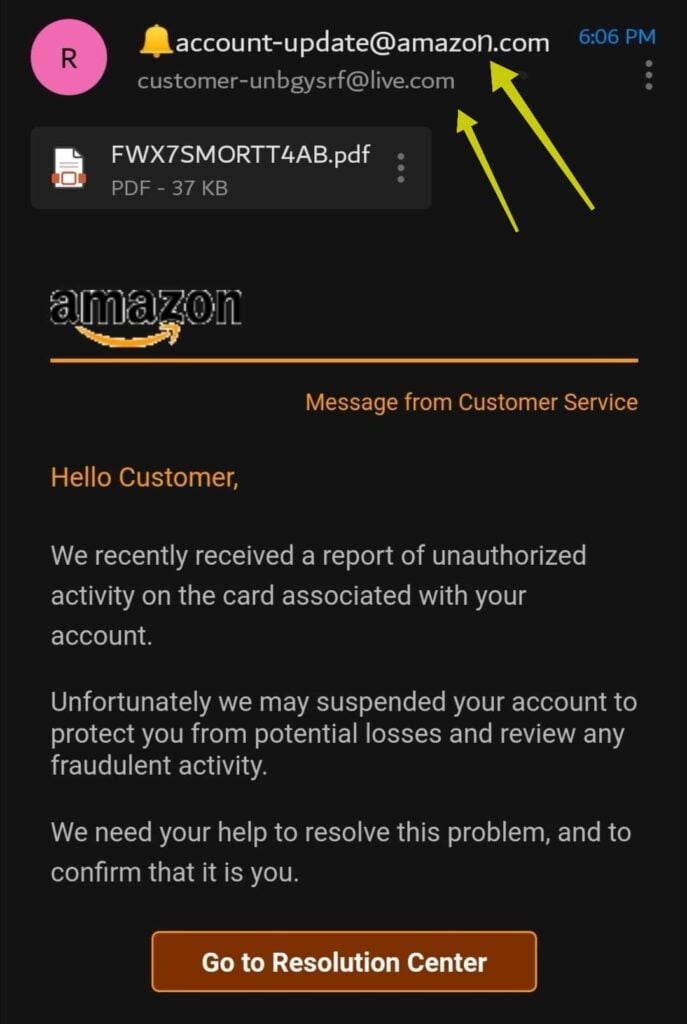
For instance, replace the “m” in something@amazon.com with “rn” to create a new email at something@arnazon.com. or replacing the “oo” in Google with “00” as in g00gle.
So always pay close attention to the sender’s address and make sure it is genuine.
Other Ways to Recognize a Phishing Email:
Remember, it is not advisable to follow the instructions stipulated in an email message if you didn’t request for the email to be sent to you yourself.
Another way to detect if an email is a phishing or scam email is through the urgency of the email message request. When the message urges you to act urgently, then that is more like a sign of phishing.
Having a lot of typographical or grammatical errors in an email is another sign that it might be a scam email.
Big companies mostly start their email message salutation with the customer’s name, like Hi John, and not with a generic salutation like Hi Customer or Hi Dear. Whenever you get a generic greeting on an email claiming to be from a reputable company, make sure you verify the email for phishing.
Always remember that reputable companies do not request your confidential information through email.
Avoid entering your login credentials, like your username and password, on a login page you opened through a link in an email.







