Phishing is a form of social engineering and a scam where attackers deceive people into revealing sensitive information or installing malware such as viruses, worms, adware, or ransomware.
It is important for us to talk more about phishing attacks because research has shown that phishing is responsible for 45% of all ransomware attacks. Making it the most common ransomware delivery method.
Phishing attacks can come in different flavors; they can happen to you through email, mal-advertisement, SMS, phone calls, physical mailing addresses, QR codes, social media, browser pop-ups, or other messaging apps DMs.
Though there are technical names for all these forms of phishing, my goal here is not to bother you with the technicalities but to give you a real-life general scenario about phishing attacks and how you can protect your personal data from them.
4 Must-Know Tips to Shield Yourself from Phishing Attacks
- Avoid making a refund to an account other than the originating deposit account.
- Don’t act on an unusual email or SMS request even if the sender matches the original sender without verification.
- When you receive an unusual notice about your online account, don’t confirm the situation through the notice, but rather through your normal ways of accessing the account.
- Be mindful of popups and overly positive reviews on social media.
Why This Guide to Phishing Protection Stands Out from the Rest
Even though there is a vast amount of information on the internet creating awareness about phishing attacks, the majority of people are still falling victim to it on a daily basis.
That doesn’t mean the information out there is not effective enough to protect you, but rather, it is because the phishing landscape changes so fast that the information cannot keep up with it.
Telling users not to click links or download files that come with an unsolicited email or SMS might sound like a good and easy-to-implement guide to protect oneself from phishing.
Also to make sure they verify sender information before responding to an email or SMS request.
But what happens when the attacker social engineers the user into soliciting for the link? Or when the sender’s address or phone number is spoofed, hacked, or stolen?
Don’t get me wrong, those are good cyber hygiene to follow, but we need more than that when it comes to phishing to be able to keep safe.
Therefore, in this post, we will be looking at the key concepts underlying phishing attacks so you will be able to notice it in whichever form it comes.
In order to achieve that, we are going to categorize phishing attacks into two broad categories based on the goal of the perpetrators. They include;
- Phishing attacks to steal user personal information or money and
- Phishing attacks that get users to perform actions that favor the attacker.
Understanding that the goal of the perpetrator may not necessarily be to get your PII or money at the initial state will definitely help you detect other forms of phishing.
Latest Phishing Attacks: Two Key Goals Explained
First, we are going to look at phishing attacks where the attacker wants the user to perform an action that favors the attacker.
These are the most common kinds of phishing attacks today.
The kinds of actions the attacker wants the victim to perform can range from downloading malware into the user’s computer to helping the attacker fulfill another phishing transaction either by helping them to collect payments or delivering a malicious payload.
Real-World Examples of Recent Phishing Attacks
1. Phishing attacks through business transactions and refund requests
These kinds of attacks happen when scammers pose as genuine customers or clients to get business owners to act as a money mule or pawn for them.
A money mule is someone who knowingly or unknowingly helps criminals launder money.
They often receive funds from illegal activities and then transfer them to other accounts or locations, making it difficult for law enforcement to trace the money’s origin.
As a small business owner, what will you do when a client emails you through your business email or phone calls genuinely requesting your business services, and after successful deal closing and payment reception, the customer claims a change of mind and now requests a refund from you into a different account, leaving a compensatory amount for you?
There are also cases where the attacker might want the victim to help them fulfill a payment to another supposed business that doesn’t accept their payment method.
The attacker may claim the other business offers a service to them without you knowing they are both partners in the crime.
The request might come after making an initial advance payment to your business.
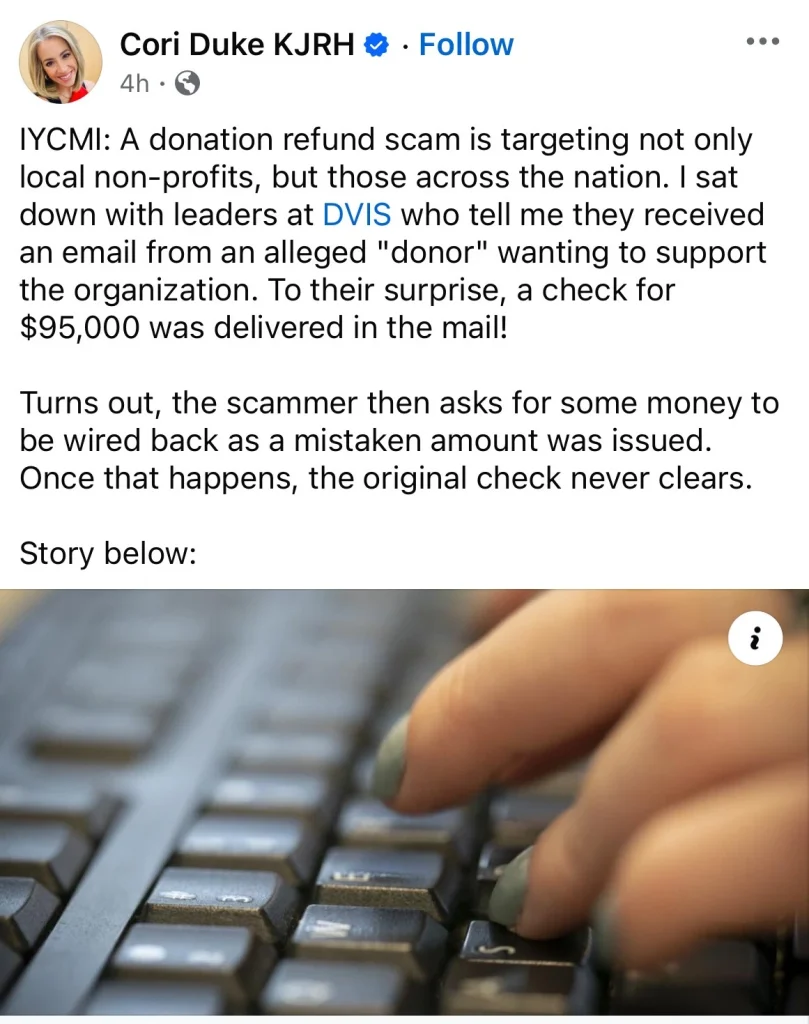
The last but not least scenario is when the attacker claims to have made a high amount of donation to your NGO and requests a refund for the excessive amount.
Here the bad actor might make their victim send the NGO $700 while they then claim they wanted to donate $100, thereby looking for a refund of $600.
The NGO scam can come in another form where the scammer sends in a check for certain huge amounts and claims they made a mistake and is requesting some portion of the amount to be wired back.
In this case, the perpetrator is looking at getting the victim to wire the refund before clearing the check, which in most cases will not get cleared.
The only way to avoid falling victim to these kinds of attacks is to avoid making refunds to a different account other than the account the money initially came from.
This will help you to avoid being a money mule or a pawn in the hands of the bad actors.
If you are not careful, this kind of skim can put your business into unnecessary legal consequences, account seizure and freeze, and reputation damage.
2. Phishing attacks through employment offers
This form of attack comes with job offers that involve fulfilling package delivery and check forwarding at an enticing wage.
These phishing attacks are aimed at job seekers, and the goal here is mostly to use the victim as a money mole or a payload deliverer.
Be careful about online or remote job offers that promise easy money with minimal work. You may be used as a middleman for delivering packages, checks, or money for cybercriminals.
If your old friend or social media connection wants to collect a payment or make a payment to someone through you, please be careful.
Now let us look at some examples of phishing scenarios that target users’ information. These include:
1. Phishing Attacks Through Physical Mailing Address
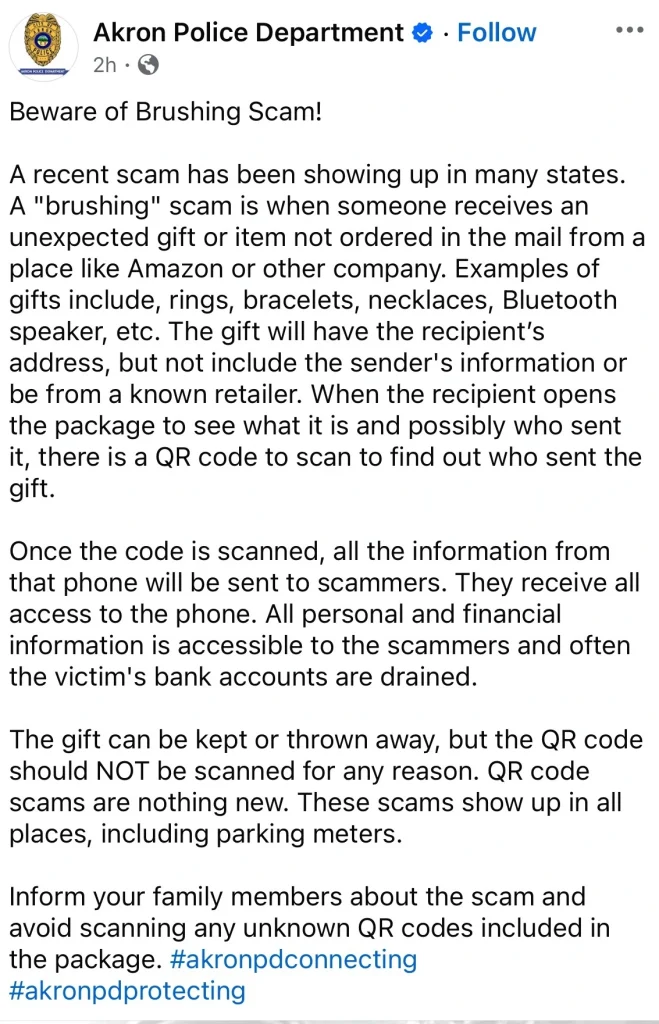
This is a scenario where you receive a package to your home mailbox without the sender’s address with a QR code to scan to find out who sent the gift.
When you mistakenly scan the QR code to find out the sender, the scammer will steal your personal information from your phone. They can also receive all access to your phone, thereby possibly draining your bank account or gaining access to your other online accounts.
This form of attack mimics the e-commerce brushing scam, where the perpetrator uses it to increase their product reviews and lure unsuspected buyers.
Making sure not to scan QR codes on packages you did not order will protect you from this kind of attack.
2. Phishing through fraud protection helps.
In this form of scam, the attacker claims to be the good guy.
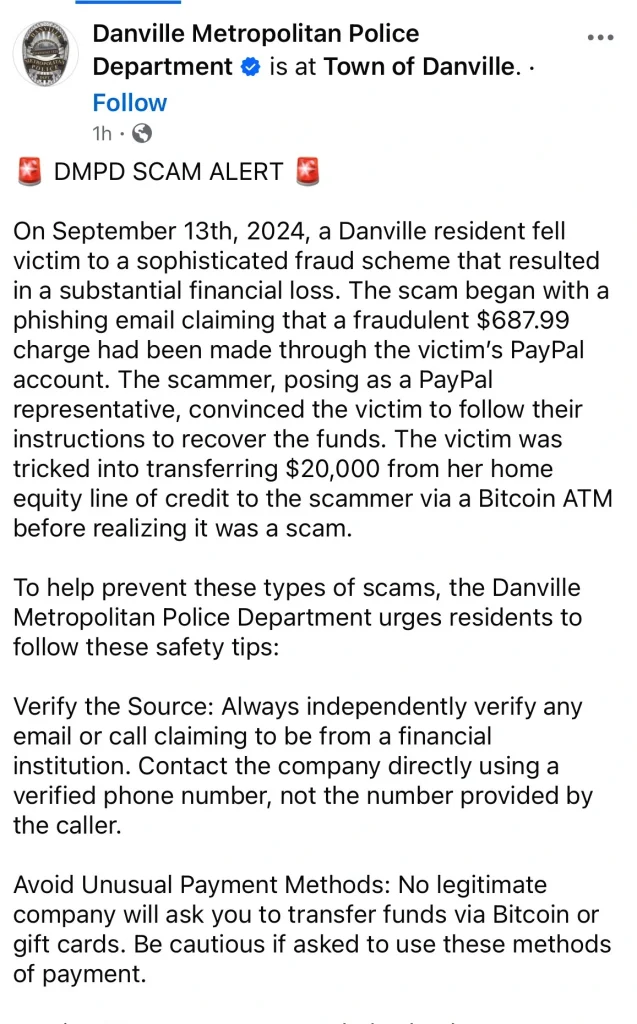
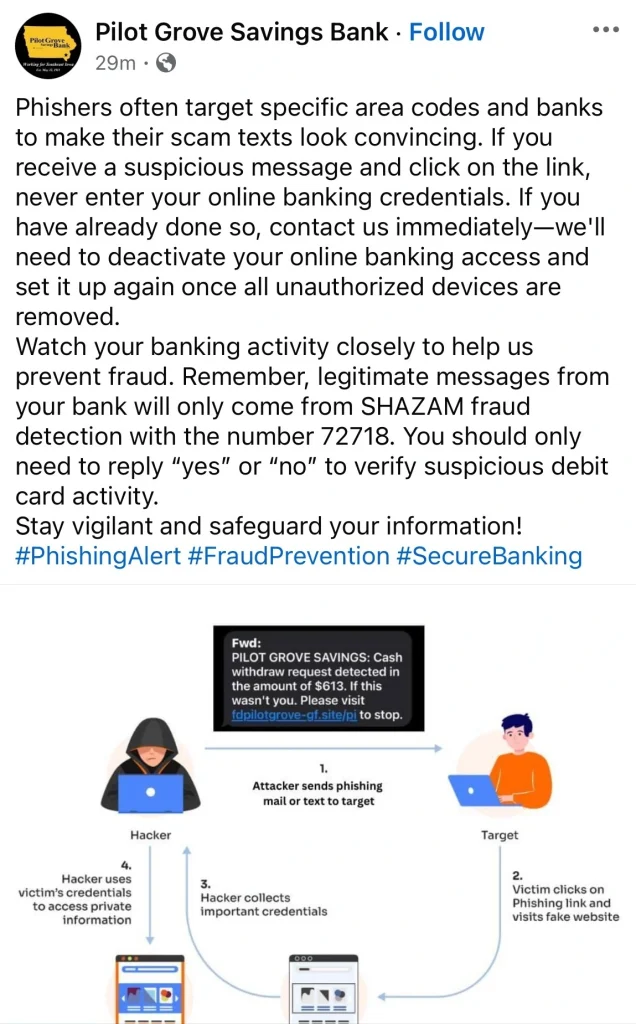
They reach out to you claiming money has been stolen from your bank account or fintech platform account like PayPal or Cash App.
On some occasions, they might implement a fake debit alert to make the whole scam look real.
Or they might use an SMS alert that looks similar to your bank’s fraud alert.
In order to avoid falling victim to such a scam, you will have to avoid interacting with anything related to the message or alert you received.
The best thing to do is to login into your account through your bank app the way you normally do to verify the situation of things or use your bank or fintech platform’s official customer care number to verify the situation of things with your account.
Don’t click or respond to the suspicious alert or email.
3. Phishing using personalized information
This form of phishing has some accurate information about their target that can make them look credible and believable.
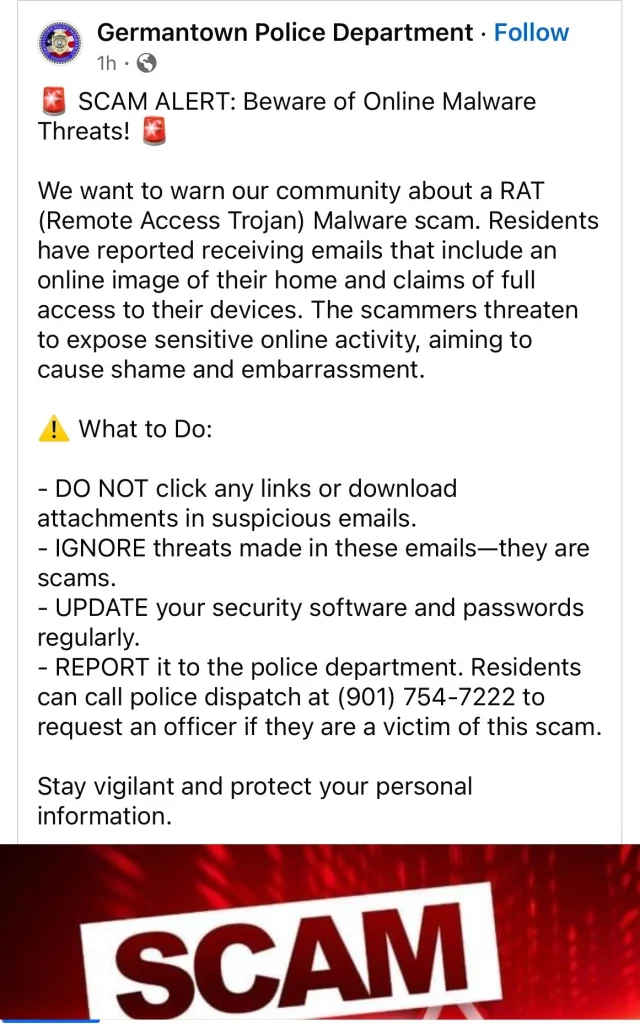
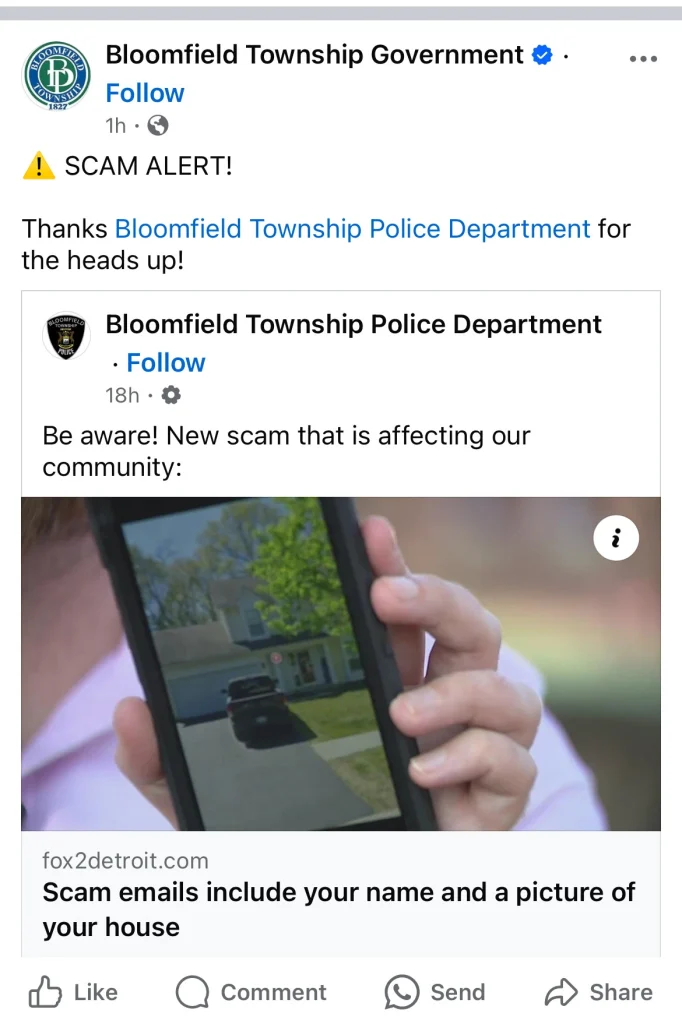
It can come in the form of blackmail, where the scammer claims to have access to your home network and has some sensitive information about your online activities.
In order to make their claims look real, the attacker might attach a picture of your house to the email or message to you.
This form of phishing works well with sextortion scams. It can also come in various shapes and tricks. It may be an email with your personal information urging you to claim a free offer or a win.
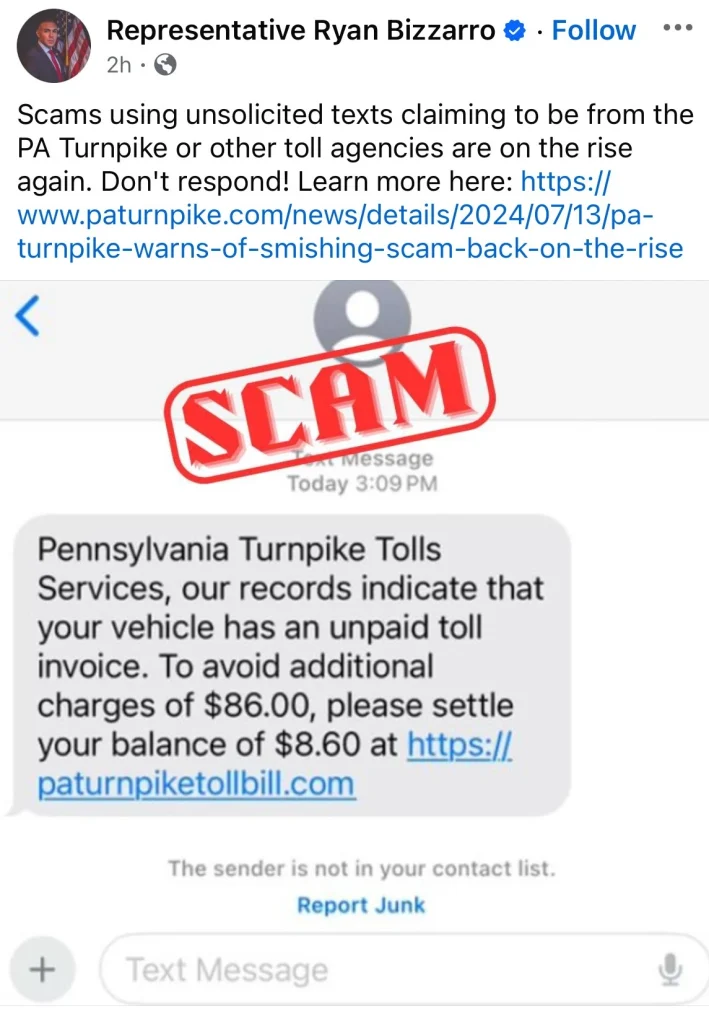
4. Phishing using payment default penalty
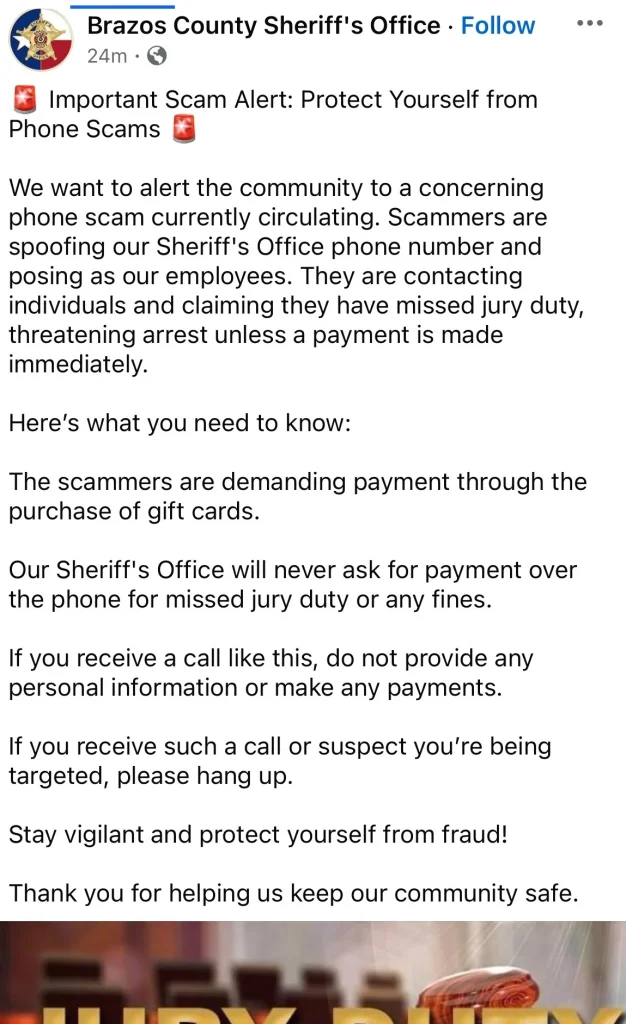
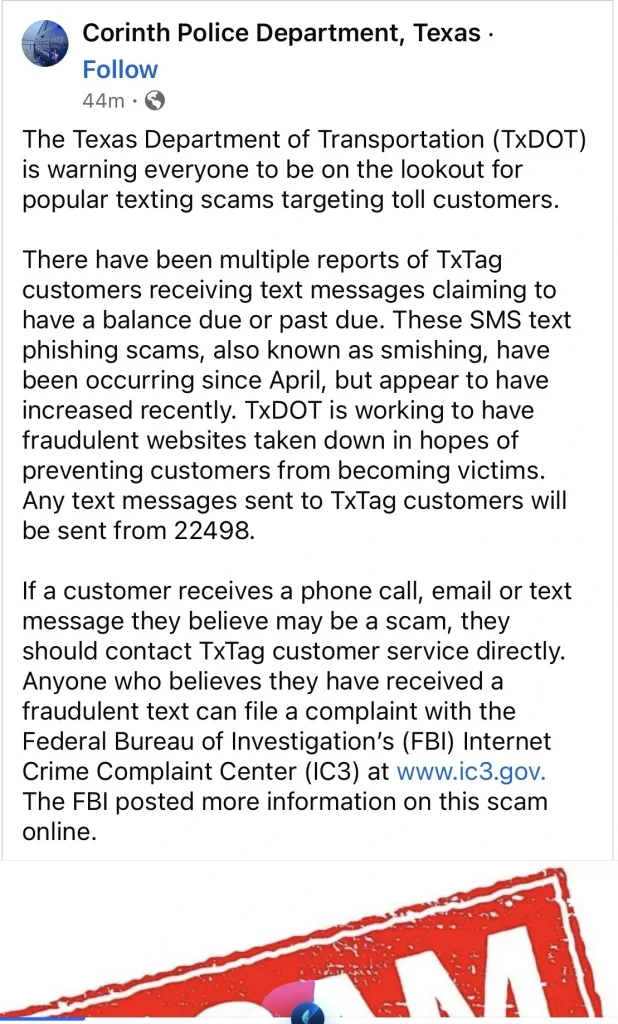
This form of phishing example comes with a message that claims that your payment is due or provides you with a scam link or method to fulfill the payment.
Sometimes, this message or email can come through a spoofed account. This makes it difficult for victims to differentiate it from the original address.
One tool this kind of scam uses well is persuasion and urgency with the claim of a severe penalty if the victim doesn’t act quickly or comply with their demands.
This kind of scam can claim to come from any genuine office that your details might be attached to, like a toll office, police department, or hospital.
5. Phishing through in browser pop-ups or social media positive reviews.
Phishing can come through bogus or hoax alerts on your computer while browsing the internet.
It can come as a fake alert telling you that your system has been infected by a virus or a full-window alert telling you that you have been infected by ransomware, giving you an email or phone number to contact.
The attacker’s aim here is to get you to click or download malware onto your device, enabling them to steal your information.
It can also come as positive reviews or comments under social media posts or advertisements. This is for the scammer to earn some credibility in order to scam you.
Making sure not to be gullible to such reviews or pop-ups is the only way to overcome such scams.
Remember, we can not exhaust all forms of phishing attack scenarios, phishing attacks can come in different flavors. The one thing you can do to overcome this is to develop a normal way of your daily operations and be very careful when things outside the normal come up.
Always use your default mode to verify the situation.
For instance, if you receive an alert that your bank account is hacked, make sure you follow your usual way to login into your account to verify if it is true, and if you are the type that visits your bank branch, visit your nearest branch. Don’t go outside your normal practice to resolve the situation.
If you receive an email with only attached file as the message body, don’t be tempted to open or download the file. Simply delete the email except if you requested for the email yourself.
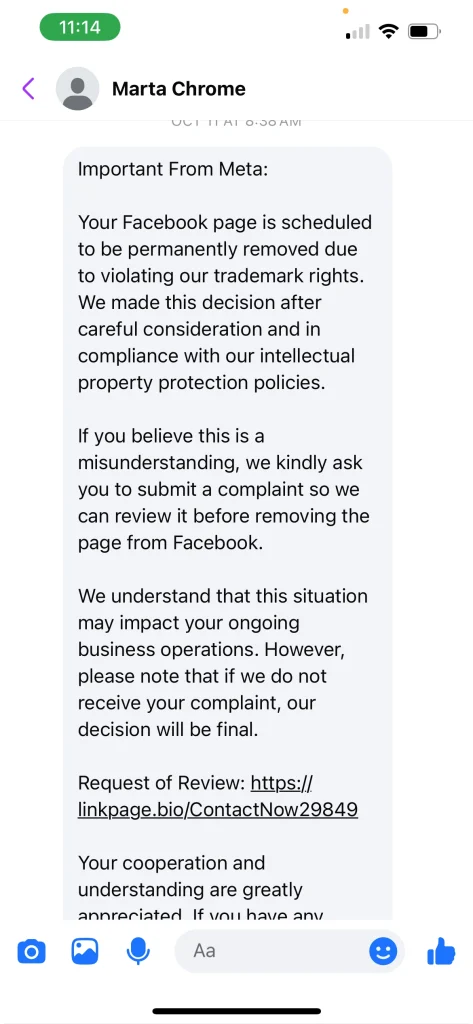
6. Phishing Using Social Media Account Disable Warning
This kind of attack targets business owners and individuals that use social media for business or to run ads. Here the bad actor creates a social media account with the names that can convince their victim that they are messaging them from the social media platform support, like “Supports Page,” or in some occasions, they might use individual names and use the account to send warning messages to unsuspecting users.
The content of their message is mostly to scare users that their account is about to be disabled or permanently deleted, asking them to request a review through a link or reach support.
In order to avoid falling victim to this kind of attack, you need to know the official channels used by the social media platform to communicate account issues with the user. For instance, the Meta official channel is either through email (remember to confirm the email address before acting on the message), in-app notifications, or through the Facebook support inbox.
Whenever you start receiving such messages from a personal profile, know that they are phishing scams and report them to Meta.
7. Phishing Using Social Media Advert
Scam advertisements on social media are one way bad actors perpetrate their phishing scam. Remember, just because it said sponsored doesn’t mean it is legit. So, don’t lower your guard because of that.
Pay attention to links associated with an ad and make sure it is legit and leads to the actual company domain. Also analyze the advertisement promise to see if it is a hoax or not.
How to Protect Yourself from Phishing Attacks
There are some popular advices on ways you can protect yourself from phishing attacks that are out there in the public domain, like;
- Be wary of unexpected or unsolicited emails or SMSs.
- Verify sender addresses.
- Look for suspicious links.
- Never provide personal information through email, mail, call, or SMS.
- Use strong, unique passwords.
As you keep those in mind, also make sure you remember the following;
- Avoid making a refund to an account other than the originating deposit account.
- Don’t act on an email or SMS request even if the sender matches the original sender without verification through an additional medium.
- When you receive an unusual notice about your online account, don’t confirm the situation through the notice, but rather through your normal ways of accessing the account.
- Be mindful of popups and overly positive reviews on social media.







