Public charging stations may seem like a modern convenience, especially when your phone battery is low and you are far from home. Found in airports, cafes, shopping malls, and hotels, these charging ports offer quick relief. But beneath the surface lies a growing cyber threat that most users do not expect.
Cybercriminals have figured out how to turn these helpful charging stations into silent gateways for malware, spyware, and data theft. The practice is known as juice jacking. In this guide, you will learn how hackers use public charging stations to plant malware and how to protect yourself every time you plug in.
What Is Juice Jacking?
Juice jacking is a type of cyberattack where hackers use USB charging ports or cables to infect devices with malware or steal data during the charging process. It combines two functions of USB ports: charging and data transfer. Once a phone is connected to a compromised port, malware can be installed without your permission or knowledge.
How Public Charging Stations Become Malicious
While not every charging port is compromised, many public charging stations lack strong security. Hackers exploit these vulnerabilities in several ways.
Compromised USB Ports
Hackers may install small hardware devices inside public charging kiosks. These devices can transfer spyware or keyloggers onto connected phones, download sensitive data such as contacts, photos, or passwords, and monitor keystrokes and activity after infection.
Infected Charging Cables
In some cases, the cable itself is the weapon. Hackers may leave behind malicious cables that look normal but contain embedded hardware. Once a user plugs in, the cable begins transferring malware.
Hijacked Charging Stations
Cybercriminals can hack into a charging station’s software to load malware onto multiple connected devices simultaneously. These setups often appear legitimate, making them difficult to detect.
Real-World Incidents and Warnings
Cybersecurity experts and federal agencies have issued public warnings about juice jacking:
- In 2023, the Federal Bureau of Investigation (FBI) posted alerts advising people not to use public USB charging stations due to increased reports of compromised ports.
- Security researchers demonstrated OMG cables capable of executing remote commands and bypassing device defenses.
- Multiple travelers at airports and train stations have reported unexplained device behavior after charging through public ports.
These examples are not just theory. They reflect real, growing threats that could affect anyone with a smartphone.
What Malware Can Do Once Installed
If a hacker successfully plants malware through a charging station, the consequences can be serious. Spyware records your activity and sends it to attackers. Keyloggers capture your typed passwords and messages. Ransomware locks your files and demands payment to unlock them. Backdoors give hackers continuous remote access to your device. Credential theft enables access to your banking, email, or cloud storage.
The attack is silent. Most victims do not realize anything happened until their data is exposed or their device slows down due to malicious background activity.
How to Know If Your Device Has Been Compromised
It is not always easy to detect malware from a charging attack, but some symptoms include:
- Device slows down or heats up abnormally
- Unexpected pop-ups or unfamiliar apps appear
- Increased data usage without clear reason
- Battery drains faster than usual
- Login sessions expire, or you are logged out of important accounts
- Strange behavior from apps that were previously stable
If any of these occur after charging from a public port, consider running a security scan and checking for unauthorized changes.
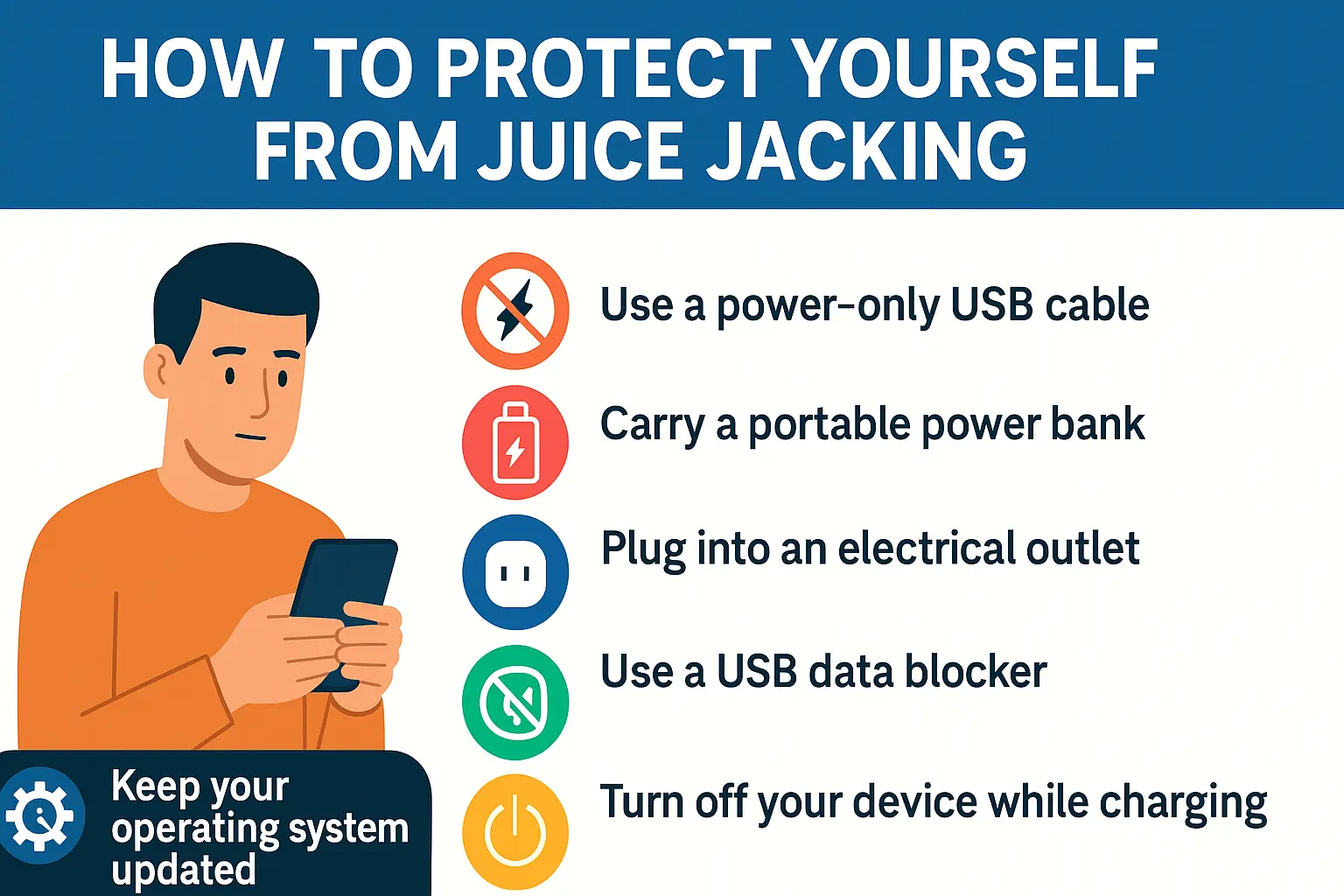
How to Protect Yourself from Juice Jacking
You can still keep your phone charged safely in public. Use the following strategies to protect yourself.
Use a Power-Only USB Cable
A charge-only cable is built to disable data transfer. These cables deliver power but block any attempt to send or receive data.
Carry a Portable Power Bank
A personal power bank gives you complete control. Charge it at home, then use it to recharge your phone on the go without relying on unknown ports.
Plug Into an Electrical Outlet
If available, use a regular wall outlet with your original charging adapter. These do not support data transfer and are much safer than public USB ports.
Use a USB Data Blocker
This device connects between your cable and the port, physically blocking the data pins and allowing only electricity to pass through.
Turn Off Your Device While Charging
Powering down your phone before connecting it to a public USB port can reduce risk. However, this is not foolproof if the port is aggressively designed to bypass security.
Keep Your Operating System Updated
Regular updates include patches for known vulnerabilities. An updated device is harder to compromise, even during brief data exposure.
What to Do If You Suspect Your Phone Has Been Infected
If you believe your device may have been affected by juice jacking:
- Disconnect the phone immediately
- Run a mobile security scan using trusted apps like Malwarebytes or Bitdefender
- Delete suspicious apps or files
- Clear cache and browser history
- Change all important passwords from a clean device
- Perform a factory reset if malware persists
Do not ignore the signs. Early action limits damage and prevents deeper compromise.
Final Thoughts
Public charging stations are convenient, but they come with hidden dangers. Juice jacking may not be the most talked-about cyber threat, but it is real, it is growing, and it preys on simple habits. Hackers know users will choose the fastest charging option, even if that means compromising their security.
Now that you know how hackers use public charging stations to plant malware, you can avoid the trap. Bring your own power source. Use safe cables. Stay alert. Your phone holds your life. Protect it with every charge.