One way hackers can get at you is through the security vulnerability in the operating system or applications you use.
Time has passed when all you need to enjoy adequate cybersecurity is just to keep your username and password safe.
We are in a time and season where security vulnerabilities that come with the operating systems or applications we use are enough for an attacker to hack us.
Vulnerability is simply a flaw in software or hardware design or the underlying programming code that allows a bad actor to make the affected system do something that wasn’t intended.
Some of these security vulnerabilities might come from flaws in the operating system design or the browser application we use. It might also come from the websites we visit.
Whenever the technology you use has common security flaws, every other security measure you take is simply a waste of effort until it is patched.
This is why it is advisable for you to know the security vulnerability of the tech tools you use and update your phone or computer applications regularly.
In this post, I will share with you two websites where you can check the security vulnerability level of the technologies you use.
These are websites every cyber security-conscious person should visit at least once a week to understand their security vulnerability status. They are;
1. National Vulnerability Database (NVD)
This website lists and keeps track of publicly disclosed vulnerabilities in all kinds of software and hardware products.
They identify each new vulnerability with a common vulnerability and exposure (CVE) name or identifier. The CVE name looks like this – CVE-2020-5678.
2020 in the CVE name represents the year the vulnerability was discovered and the other numbers 5678 is the vulnerability identifier.
The website contains a list of newly discovered vulnerabilities of different products.
How to Use the National Vulnerability Database
The best way to use the NVD is to search for the product you want to check its vulnerability by its name, the vendor name, or by CVE name.
Let assume you use Windows 10 operating system or Facebook. You might decide to check the vulnerability for the product by typing the product name as your search keyword.
To check the security vulnerabilities of your products; simply click HERE to be taken to the NVD search website which will display the webpage below.
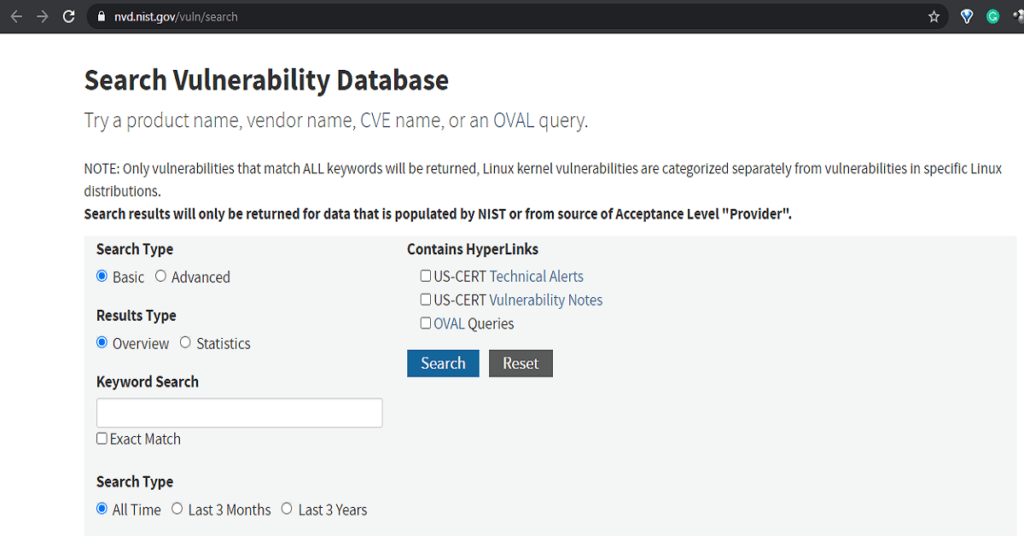
Type in your keyword search on the Text box provided. This can be the name of the product like Windows 10.
Then check the Exact Match checkbox if you want it to give you only the results pertaining to Windows 10.
Also, check the Contains Hyperlinks checkboxes to get additional information links about the vulnerability and its patches. Then click Search.
After some minutes a page will display with a list of security vulnerabilities associated with the product with their CVE names.
Related Post: Data Security- How to Find Out What Hackers Already Know About You
2. Common Vulnerabilities and Exposures (CVE)
This is another website with a list of publicly known information security vulnerabilities.
The list contains the CVE name and information like the attack type using the vulnerability; its impact; the software components that are affected by it, and any attack vector that can make use of the vulnerability.
How to Use the CVE Website
To use the CVE search to check a product vulnerability; simply click Here.
After the web page loads, then type in your search keyword in the text box and click Submit.
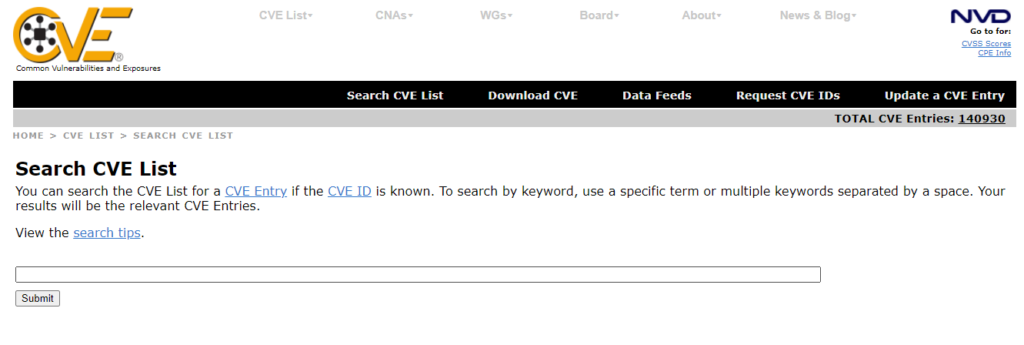
Then wait for some minutes and a list of security vulnerabilities will be displayed with their CVE names.
Related Post: Don’t Wait Until You are Hacked- The New Google Chrome Safety Check Tool.
How Data From The NVD and Search CVE List Can Help You for Your Security Decisions
One thing to look out for on a security vulnerability details is the Common Vulnerability Scoring System (CVSS) number.
This number ranges from 0.1 to 10.0. Where 10 indicates a high-risk vulnerability.
If the CVSS value of a CVE is above 7, that means the vulnerability is critical and has a high risk.
In order words, vulnerabilities with higher CVSS scores have higher probabilities of exploitation or greater impacts on systems when exploited.
You should also watch out for products with a high number of Common Vulnerabilities and Exposure per year.
This is because if you are someone that doesn’t update your device regularly, you might end up being cheap to cyber-attacks if you end up using them.
This data should also help influence your decision while procuring tech equipment for your business purposes and while making the choice of software.
Another important factor to check is how easy it is to exploit the discovered vulnerabilities of the product. This is called low access complexity. This implies that there are no special conditions for exploiting the vulnerability, such as when the system is available to large numbers of users, or the vulnerable configuration is ubiquitous.
It is not a good cybersecurity decision to go for a product or service that has more critical CVE and with a very low access complexity.
Remember, having a strong password or two-factor authentication is not a remedy for common vulnerabilities. The only way out is to patch the software or run your updates when necessary.
It is important to note that you are not the only one using these websites. Hackers can also visit it to gain knowledge of new vulnerabilities and the type of attacks to throw at you.
Make sure you update devices you use for your online transactions regularly.








Thank you for this. This article made me more cyber-knowledgeable.